Cryptography is conversion
of plain readable text into unreadable form. In cryptography first the data is converted
into cipher text (that is encryption) and then the cipher text is converted
back into readable form (that is decryption). Cryptography basically works on
the concept of encryption and decryption. Encryption and decryption should not
be confused with encoding and decoding, in which data is converted from one
form to another but is not deliberately altered so as to conceal its content.
Encryption is achieved through the algorithms. These algorithms are works with
logic, mathematic calculations and its complexities.
Hash Function is most
important function in Cryptography. A hash means a 1 to 1 relationship between
data. This is a common data type in languages, although sometimes it’s called a
dictionary. A hash algorithm is a way to take an input and always have the same
output, otherwise known as a 1 to 1 function. An ideal hash function is when
this same process always yields a unique output. So you can tell someone, here
is a file, and here is its md5 hash. If the file has been corrupted during
then the md5 hash will be a different value.
In practice, a hash function
will always produce a value of the same size, for instance md5 () is will always
return 128bits no matter the size of the input. This makes a 1 to 1
relationship impossible. A cryptographic hash function takes extra precautions
in making it difficult to produce 2 different inputs with the same output, this
is called a collision. It also makes it difficult to reverse the function. Hash
functions are used for password storage because if an attacker where to
obtain the password's hash then it forces the attacker to break the hash before
he can use it to login. To break hashes, attackers will take a word list or an
English dictionary and find all of the corresponding hash values and then
iterate though the list for each password looking for a match.
md5 (), sha0 and sha1 () are
all vulnerable to a hash collision attacks and should never be used for
anything security related. Instead any member of the sha-2 family, such as
sha-256 should be used.
To calculate Hash Value,
we will use Hash Calculator. Install Hash Calculator from --> http://www.slavasoft.com/hashcalc/
Hash function plays major
role in hacking/forensic world because it helps us to know whether a particular
file has changed or not. You can also calculate hash value of your computer and
know if anyone has made any kind of changes.
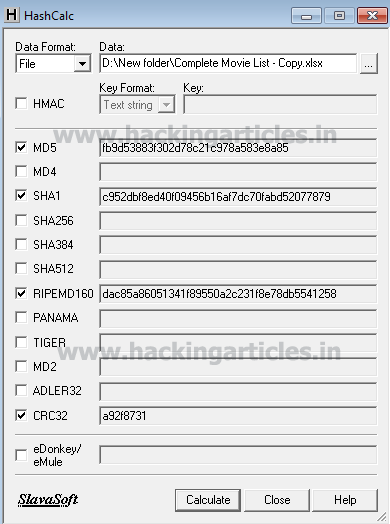
To calculate hash value open
Hash Calculator.
Now browse
the file of which you want to calculate the hash value. And click on
Calculate.
After clicking on
calculate it will give too hash values using four different hashing algorithms
i.e MD5, SHA1, RIPEMD160, CRC32. You can check other boxes too if you want to
use those algorithms to calculate hash value.
This way Hash
calculator helps us to know the hash value. Now if there are any changes made
in this file, the hash value will change too.
Once I calculated
the hash value above i made some changes in the file and calculated the hash
value again with the same method and as a result the hash value was changed.
Seeing these two
values of MD5 of the same file we can conclude that some changes are made.
Because even slightest difference will change the hash value.
But now the main
question is how to detect this change because a file can be of 1TB too. Also
imagine that you are sending a harddisk full of important documents to someone
and there is a huge possibility that someone can bribe the sender and make
changes in your documents. So how can you detect these changes?
The answer is very
simple --> Compare it! This tool helps us achieve
our goal which is to detect the change.
Download Compare it!
From -->http://www.grigsoft.com/wincmp3.htm
Open Compare it!
Click file
and a drop menu will appear. Select compare files option.
A Dialogue box
will open which will ask you to choose the files that you want to compare.
Click on Browse button and select your file. And click on Open.
It will show you the
changes by highlighting them with green color and the red color will tell the
exact change as shown below:
So, in such way you
can protect your sensitive data and detect the crime done too.