In the previous article of
tcpdump, we learned about some basic functionalities of this amazing tool
called tcpdump. If you haven’t check until now, click here. Hence, in this part, we will cover some of
the advance options and data types. So that we can analyze our data traffic in
a much faster way.
Table of Content
·
Link level header
·
Parsing and printing
·
User scan
·
Timestamp precision
·
Force packets
§ RADIUS
(Remote Authentication Dial-in User Service)
§ AODV
(Ad-hoc On-demand Distance Vector protocol)
§ RPC
(Remote Procedure Call)
§ CNFP
(Cisco NetFlow Protocol)
§ LMP
(Link Management Protocol)
§ PGM
(Pragmatic General Multicast)
§ RTP
(Real-Time Application Protocol)
§ RTCP
(Real-Time Application Control Protocol)
§ SNMP
(Simple Network Management Protocol)
§ TFTP
(Trivial File Transfer Protocol)
§ VAT
(Visual Audio Tool)
§ WB
(Distributed White Board)
§ VXLAN
(Virtual Xtensible Local Area Network)
·
Promiscuous mode
·
No promiscuous mode
Link level header
Tcpdump provides us the option to
showcase link-level headers of each data packets. We are using -e parameter to
get this information in our data traffic result. Generally, by using this
parameter, we will get MAC address for protocols such as Ethernet and IEEE
802.11.
tcpdump -i eth0 -c5
tcpdump -i eth0 -c5 -e
Parsing and printing
As we all know that, the
conversation of a concrete syntax to the abstract syntax is known as parsing.
The conversation of an abstract syntax to the concrete syntax is called
unparsing or printing. Now to parse a data packet we can use -x parameter and
to print the abstracted syntax, we can use -xx parameter. In addition to
printing the headers of each data packets, we can also print the packet in hex
along with its snaplen.
tcpdump -i eth0 -c 2 -x
tcpdump -i eth0 -c 2 -xx
If we want this information provided
by -x parameter along with their ASCII code then we need to use -X parameter
and if we want the results of -xx parameter along with their ASCII codes then
we need to use -XX parameter. To use these parameters in our Data analysis, use
the following commands:
tcpdump -i eth0 -c 2 -X
User scan
If we are running tcpdump as a
root then before opening any saved file for analysis, you will observe that it
changes the user ID to the user and the group IDs to the primary group of its
users.
Tcpdump provides us -Z parameter,
through which we can overcome this issue but we need to provide the user name
like the following:
tcpdump -i eth0 -c 2 -Z root
tcpdump -i eth0 -c 2 -Z kali
There is one more way to do this,
i.e. with the help of –relinquish-privileges= parameter.
Timestamp precision
Timestamp is the time registered
to a file, log or notification that can record when data is added, removed,
modified or transmitted. In tcpdump, there are plenty of parameters that move
around timestamp values like -t, -tt, -ttt, -tttt, -ttttt, where each parameter
has its unique working and efficiency.
·
-t parameter which must don’t print a
timestamp on each dump line.
·
-tt parameter which can print timestamp
till seconds.
·
-ttt parameter which can print a
microsecond or nanosecond resolution depending upon the time stamp precision
between the current and previous line on each dump line. Where microsecond is a
default resolution.
·
-tttt parameter which can print a
timestamp as hours, minutes, seconds and fractions of seconds since midnight.
·
-ttttt parameter which is quite similar
to the -ttt parameter. It can able to delta between current and first
line on each dump line.
To apply these features in our
scan we need to follow these commands:
tcpdump -i eth0 -c 2
tcpdump -i eth0 -c 2 -t
tcpdump -i eth0 -c 2 -tt
tcpdump -i eth0 -c 2 -ttt
tcpdump -i eth0 -c 2 -tttt
Force packets
In tcpdump, we can force our scan
of data traffic to show some particular protocol. When using the force packet
feature, defined by selected any “expression” we can interpret specified type.
With the help of the -T parameter, we can force data packets to show only the
desired protocol results.
The basic syntax of all force
packets will remain the same as other parameters -T followed by the desired
protocol. Following are some protocols of force packets:
·
RADIUS – RADIUS stands for Remote
Authentication Dial-in User Service. It is a network protocol, which has its
unique port number 1812, provides centralized authentication along with
authorization and accounting management for its users who connect and use the
network services. We can use this protocol for our scan.
tcpdump -i
eth0 -c5 -T radius
·
AODV – Adhoc On-demand Distance Vector
protocol, is a routing protocol for mobile ad hoc networks and other wireless
networks. It is a routing protocol that is used for a low power and low data
rate for wireless networks. To see these results in our scan follow.
tcpdump -i
eth0 -c5 -T aodv
·
RPC – Remote procedure call, it is a
protocol that one program can use to request service from a program located in
another computer on a network without having to understand the network details.
A procedure call is also known as a function call. For getting this protocol in
our scan use the following command:
tcpdump -i
eth0 -c5 -T rpc
·
CNFP – Cisco NetFlow protocol, it is a
network protocol developed by cisco for the collection and monitoring of
network traffic, flow data generated by NetFlow enabled routers and switches.
It exports traffic statistics as they record which are then collected by its
collector. To get these detailed scans follow this command.
tcpdump -i
eth0 -c5 -T cnfp
·
LMP – Link Management Protocol, it is
designed to ease the configuration and management of optical network devices.
To understand the working of LMP in our network, we need to apply this protocol
in our scan.
tcpdump -i
eth0 -c5 -T lmp
·
PGM – Pragmatic general multicast, it is
a reliable multicast network transport protocol. It can provide a reliable
sequence of packets to multiple recipients simultaneously. Which further makes
it suitable for a multi-receiver file-transfer. To understand its working in
our data traffic follows.
·
RTP – Real-time application protocol, it
can code multimedia data streams such as audio or video. It divides them into
packets and transmits them over an IP network. To analyze this protocol in our
traffic we need to follow this command:
tcpdump -i
eth0 -c5 -T rtp
·
RTCP – Real-time application control
protocol, this protocol has all the capabilities of RTP along with additional control.
With the help of this feature, we can control its working in our network
environment. To understand the working of this protocol in our data traffic
apply these commands.
tcpdump -i
eth0 -c5 -T rtcp
·
SNMP – Simple Network Management
Protocol, is an Internet standard protocol for collecting and organizing
information about managed devices on IP networks for modifying that information
to change device behavior. To see its working in our traffic, apply this command.
tcpdump -i
eth0 -c5 -T snmp
·
TFTP - Trivial File Transfer Protocol, is
a simple lockstep File transfer protocol that allows its client to get a file
from a remote host. It is used in the early stages of node booting from a local
area network. To understand its traffic, follow this command.
tcpdump -i
eth0 -c5 -T tftp
·
VAT - Visual Audio Tool, is developed by
Van Jacobson and Steven McCanne. It is an electronic media processing for both
sound and a visual component. To understand its data packets in our traffic we
need to apply these commands.
tcpdump -i
eth0 -c5 -T vat
·
WB – Distributed whiteboard, the program allows
its users to draw and type the messages onto canvas, this should be synchronized
to every other user that is on the same overlay network for the applications.
New users should also receive everything that is already stored on the
whiteboard when they connect. To understand its data packets, follow this
command.
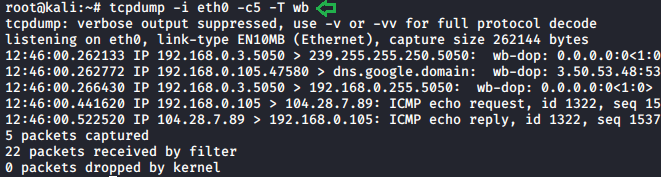
tcpdump -i
eth0 -c5 -T wb
·
VXLAN - Virtual Xtensible Local Area
Network, is a network virtualization tech that attempts to address the
scalability problems associated with a large cloud computing area. It is a proposed Layer 3 encapsulation protocol that will make it easier
for network engineers to
scale-out cloud computing. To understands its data traffic follows these
commands.
tcpdump -i
eth0 -c5 -T vxlan
These are some of
the protocol which is used under forced packets parameter to get the fixed desired
data traffic from scan.
Promiscuous Mode
In computer networks, promiscuous
mode is used as an interface controller that will cause tcpdump to pass on the traffic it receives to the CPU rather than passing it
to the promiscuous mode, is normally used for packet sniffing that can take
place on a part of LAN or router.
To
configure promiscuous mode by following these commands.
ifconfig
eth0 promisc
ifconfig
eth0
After
enabling the promiscuous mode in our network, let us capture some packets with
the help of this by applying these commands.
No
Promiscuous Mode
In the
previous parameter, we learned about the promiscuous mode that means a network
interface card will pass all frames received to the OS for processing versus
the traditional operation where only frames destined for the NIC’s MAC address
or a broadcast address will be passed up to the OS. Generally, promiscuous mode
is used to “sniff” all traffic on the wire. But if we want to switch to
multicast mode against the promiscuous mode. Then we need to use
–no-promiscuous-mode parameter, which helps us to which the mode without
changing the network settings.
tcpdump
-i eth0 -c 5 --no-promiscuous-mode
This is
the second part of the series. So, get familiar with these features and stay
tuned for some advance features of tcpdump in our next article.