Shellphish is an interesting
tool that we came across that illustrates just how easy and powerful phishing
tools have become today. The tool leverages some of the templates generated by
another tool called SocialFish. The tool offers phishing templates for 18
popular sites, the majority are focused on social media and email providers.
There is also an option to use a custom template if so desired.
Similarly you can generate another duplicate page i.e NETFLIX as shown below.
We delete the “Reset Password” button, highlight where it says “password” in the “Secure your account by resetting your password now.”.
Table of Content
Phishing and Social
Engineering
Installation
Exploring Templates
- Instagram
- Netflix
- Twitter
Weaponization
Phishing Attack
Phishing and Social Engineering
Phishing is
probably one of the biggest issues for most organizations today, with network
and endpoint defensive technology getting better and better, the bad guys
aren’t trying to go after the though route and instead going for the low
hanging fruit. Phishing is one of those issues where training the employees is
your best defense – try your best to make sure they can spot a malicious email
and make sure that they can report it easily so that appropriate action can be
taken as quickly as possible. The train of thought behind saying this is that –
it’s beneficial to depend on multiple nodes of human intelligence to spot a
potential threat, because even if one person spots and reports a phishing mail,
its possible to run mass searches and find who all were targeted by a campaign.
Social engineering is a very interesting subject to think about, in this context, it is
basically using the victim’s familiarity and habits against them. Human beings
are creatures of habit, we are so used to certain things in our life that when
faced with them, we don’t think twice before acting on them.
As an example; we are aware
that there are a lot of attempts to by hackers to compromise social media
accounts, so if one receives an email from your preferred social media site
that there was an attempt to break into your account or an email to review your
accounts security settings, most people will click on the link and log into
their account to check what’s going on. A hacker will use this against a
victim, all they need to do is swap a real link with a malicious one.
Shellphish is probably one of the easiest ways to generate that malicious link.
Let’s have a look.
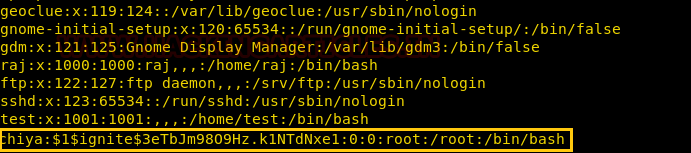
Installation
Shellphish is fairly straight
forward to install. It can be done on your Linux of choice, we will be using
Kali. We fire up our Kali Linux and use the terminal to navigate to the
desktop.
cd Desktop
We need to clone the
ShellPhish from GitHub, the download link is provided below.
git clone
https://github.com/thelinuxchoice/shellphish.git
This makes a folder named
“shellphish” on our desktop. Let’s check the folder and its contents.
ls
cd shellphish/
ls
The next step is to change
the permissions of the shellphish.sh file so that we as the admin can use it.
We don’t want everyone to have open access to it.
chmod 744 shellphish.sh
And that’s it, now we can launch our phishing tool
./shellphish.sh
Exploring
Templates
ShellPhish offers us 18 prebuilt templates, we will look
through 3 of them to get an idea of what someone on the receiving end looks at
when they get a link generated by this tool.
Get the Instagram page. The platform needs no introduction.
We can see what the malicious link leads to, the page it shows is very
convincing and might easily fool someone who isn’t paying attention,
Similarly you can generate another duplicate page i.e NETFLIX as shown below.
Weaponization
for Twitter
Now we will see what the process of weaponizing a phishing
link looks like.
Once again, let’s start ShellPhish.
./shellphish.sh
ShellPhish gives us a multitude of templates to choose from,
all we need to do is follow the prompts the tool gives us.
We will choose the “Twitter
template” for this demonstration.
4
We will be choosing option 2 here and using the Ngrok service to host our phising link,
this is what gives us the HTTPS on our phising pages. Just by choosing this
option, the tool starts a php and Ngrok server and we have our phishing link
presented to us.
2
Now that we have our link, what do we do? What would a
malicious actor do?
We won’t put in too much work into what is about to happen
next, it’s more so to demonstrate a process that is commonly used. The first
thing we need is an email send by Twitter to a user to make them aware of a
suspicious attempt to log into their account and that they should secure their
account by resetting their password. The catch here is that the user will first
have to log into their account to reset their password.
Here is our email that conveys good intentions. Notice the
“Reset Password” button.
We delete the “Reset Password” button, highlight where it says “password” in the “Secure your account by resetting your password now.”.
Click on the “Insert Hyperlink” function given in the
formatting bar. We copy the link given to us by ShellPhish in the Kali
terminal. See the section in the terminal that says, “Send this link to the
victim: https://f9935ff7.ngrok.io”.
This link is pasted in the section that says, “Web address (URL)” and we click
OK.
That’s it, we now have our weaponized email, ready to be
sent to our victim
Phishing
Attack
The victim has received the weaponized email, The moment the
“password” link is clicked, the ShellPhish tool starts showing signs of
activity. We can see that the tool gives us certain details like the IP of the
victim, the browser they are using, the country and the city they reside in,
etc.
Once the link is clicked, the victim is presented with a
twitter page where they can enter their credentials to access their account so
that they may change their password. We have volunteered to be the victim in
this demonstration and are entering our account email “raj@gmail.com” and
password “12345wetrtt”
The moment we click on the “Log in” button, we are
redirected to the actual Twitter site. Seems harmless right?
Now for the scary part, the credentials the victim entered
have been ferried away to the malicious actor in plain text. Lo and behold! The
tool proudly announces, “Credentials Found!”.
You can see the account name and password in plain text. The
thing that really stood out was the line that tells us the currency used in the
country the victim resides in, we’ll leave it to you to figure out why that is.
Declarations: This
article is posted only for educational purpose to spread awareness among people
from being trapped in Phishing attack.
This tool shows us how easy phishing attacks have become to
execute and depending on how determined a malicious actor is, there is a lot of
creativity that they can put into making the email look as legitimate as
possible. Just to give you an idea of how serious the issue of phishing is,
according to a recent report
– 3.4 billion fake emails are sent out daily!
Email firewalls mostly depend on threat intel or on the
strength of their filters which dictate how much scrutiny they exercise on each
email that hits a domain and how quick they can be to deem an email malicious.
The problem is that, if you don’t set the strength of these
filters to a balanced setting, they will flag and block more emails than you
would want, making the email firewall admins phone blow up. Not to mention the
amount of business that will be hindered.
So, that’s why internal human intelligence is a big tool at
our disposal when it comes to spotting malicious emails. There are many free
resources to educate your employees and peers on how to spot a malicious email,
this is one of those resources and probably one of the best ones around - https://phishingquiz.withgoogle.com/
As always, we at Hacking Articles hope you enjoyed this
article and share it with your collogues.
Have fun and stay ethical.
About The Author
Abhimanyu
Dev is a Certified Ethical Hacker, penetration tester, information security
analyst and researcher. Connect with him here