Exploitation in Linux Firewall using IPFire proxy.cgi RCE
Detect Hacker in Network using Android Phone
Cracking Wifi Password using Fern WIFi Cracker
Fern is a python based Wi-Fi cracker tool used for security auditing purposes. The program is able to crack and recover WEP/WPA/WPS keys and also run other network based attacks on wireless or ethernet based networks. The tool is available both as open source and a premium model of the free version. In this article we’ll be demonstrating a WPA dictionary attack using the open source version. You can check the link to download it here.
First step is to launch the tool.
If you have installed all of the requirements mentioned, you’ll be able to see
the following screen.
Now, here in the first option, the user can select the wireless interface from the drop down menu. Here, we have selected the Wlan0 interface. As you can see that fern here has automatically put the Wlan0 interface on monitor mode.
Monitor Mode: NIC cards by default are designed to only capture packets that are destined to be reached to a specific device. Monitor mode is essentially a promiscuous mode for wireless networks that allows Wi-Fi adapters to capture Wi-Fi management, data and control packets without having to associate with that access point first. Hence, by definition we can understand that raw pcap files can be captured by a wireless adapter in monitor mode and can be used for auditing and/or hacking purposes.
Once we have chosen the interface,
we’ll need to scan for access points now.
Here, observe that we have scanned a total of 18 access points.
Access Point: It is a
device that sends out wireless signals. Essentially the internet connection
from a router runs down to an access point and allows users to access the
internet using IEEE 802.11 protocol (commonly known as Wi-Fi). In our day to
day usage scenario, we have a Wi-Fi router set up at home which also serves as
a wireless access point.
SSID: Service Set
IDentifier is the name given to an access point for simplicity.
Launching the attack: Now
we can click on the discovered access point, choose a dictionary file and click
on launch attack with our chosen dictionary. It is that simple! As you can see
that we have a matched credential and received the SSID password down below.
Please note that this program is
only able to crack WPA/WEP/WPS keys only. For tools that work on stronger
encryption like WPA2 please refer to the latest article on wireless penetration
testing on Hacking Articles. Thanks for reading.
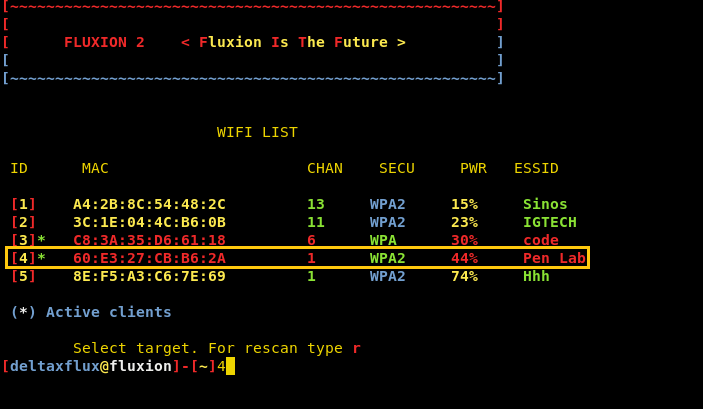
Hack Wi-Fi using Social Engineering with Fluxion (Evil Twin Attack)
- Scan the networks.
- Capture a handshake (can’t be used without a valid handshake, it’s
necessary to verify the password)
- Use WEB Interface *
- Launch a Fake AP instance to imitate the original access point
- Spawns a MDK3 process, which deauthenticates all users connected to
the target network, so they can be lured to connect to the Fake AP and
enter the WPA password.
- A fake DNS server is launched in order to capture all DNS requests
and redirect them to the host running the script
- A captive portal is launched in order to serve a page, which
prompts the user to enter their WPA password
- Each submitted password is verified by the handshake captured
earlier
- The attack will automatically terminate, as soon as a correct
password is submitted.