FLUXION is a remake of Linset by vk439 with
less bugs and more features. It’s accordant with the latest release of Kali.
This new Wi-Fi hacking method could potentially allow hackers or attackers to
recover the password key. In this method, attacker develop a new wi-fi with the
same name which is already existing. For this purpose, Fluxion is required to
create evil-twin of the target wireless network (wi-fi). Let’s see how it
works.
How it works
- Scan the networks.
- Capture a handshake (can’t be used without a valid handshake, it’s
necessary to verify the password)
- Use WEB Interface *
- Launch a Fake AP instance to imitate the original access point
- Spawns a MDK3 process, which deauthenticates all users connected to
the target network, so they can be lured to connect to the Fake AP and
enter the WPA password.
- A fake DNS server is launched in order to capture all DNS requests
and redirect them to the host running the script
- A captive portal is launched in order to serve a page, which
prompts the user to enter their WPA password
- Each submitted password is verified by the handshake captured
earlier
- The attack will automatically terminate, as soon as a correct
password is submitted.
First of all
clone Fluxion from github with command:
git
clone https://github.com/wi-fi-analyzer/fluxion.git
Now, as you have downloaded Fluxion; now
download all the tools which are required to run Fluxion as it is done in the
image below.
cd
fluxion
ls
cd
install/
ls
./install.sh
And execute the script from its folder with
command:
./fluxion
You will see the screen which is shown
below. Select your preferred language as we have chosen English by pressing 1 and press Enter.
Now, select
all channels which is option 1. It
will ask you to select the channel to listen to wi-fi connections so enter 1 to
listen to all wi-fi connections.
Now a new window will appear on your screen
which is monitoring all the wi-fi channels.AS you see your target wi-fi. Simply
hit ctrl+c to stop the search.
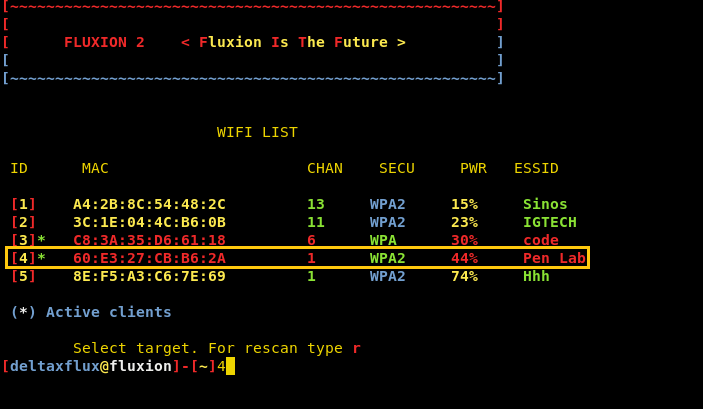
Now it will show
you a list of available targets. Select yours by pressing the id no. of that
connection as in my case I have chosen PEN
LAB by pressing 4. Now here you
will notice a change in all the target available. On id no. 3 and 4 there is an
Asterisk (*) before the mac address which represents that an increased number
of clients are attached to this wi-fi connection. For this purpose, we have
chosen id no.4
The more clients
mean the more no. of people are there who can enter the wi-fi password erroneously.
Now select option 1 for establishing Fake AP (access point) and press enter.
It will generate a Fake wi-fi AP.
Now you can simply press ENTER to save the
.cap file at default location i.e. /root/Desktop/fluxion.cap all may provide
the path to save the .cap file at destination location.
Now select option 1 to De authenticate all clients which are attached to the
target wi-fi. Here Deauth all is representing that it is sending a small DOS attack
and all the clients who are connected to the wi-fi will be disconnected
automatically.
Now select 1 for CAPTURE HANDSHAKE; you will see 2 windows, one for capturing WPA
handshake and other for DE authenticate all clients. Now enter 1 on the MENU
window to check handshake without closing the other ones.
Now, enter 1 for selection of Create a
SSL certificate.
Again choose 1 for WEB INTERFACE.
Now it will ask
you to choose the language, so select 1
for English and enter.
Now it will show
you the 4 different windows starting the fake
AP and DE authenticating the clients of the wi-fi network. For instance;
now the clients will see 2 wi-fi AP under the same name.
When victim will
connect to fake AP it will ask to enter the Password to reconnect with network.
The moment one will enter the password; you
will see a screen with the password entered by the victim.
Now; as shown in
the image above we have got our key or password “ignite@123” through FLUXION
which is the best and trouble-free straightforward method of cracking the wi-fi
password.