With MOBILedit Forensic you can view, search or
retrieve all data from a phone with only a few clicks. This data includes call
history, phonebook, text messages, multimedia messages, files, calendars,
notes, reminders and raw application data. It will also retrieve all phone
information such as IMEI, operating systems, firmware including SIM details
(IMSI), ICCID and location area information. Where possible MOBILedit Forensic
is also able to retrieve deleted data from phones and bypass the passcode, PIN and
phone backup encryption.
Note: USB Debugging must be
enabled.
Download the MOBILedit!
Forensic from here
& Install on your PC. Now Click on MOBILedit! Forensic.
Click on Connect Option. MOBILEedit! Forensic Wizard will
run and ask for Phone, Data file or SIM Card. Select Phone Option.
Click on Next.
Now it will ask for type of connection. Select Cable Connection. And click on Next.
Now follow the instructions such as install Driver or
turn on USB debugging if connecting Android.
Now connect the phone via data cable. If prompted choose
connection mode to PC Sync or COM port. Click on Next Option.
It will show the connected mobile. Check your Mobile model
and click on Next.
To
take the Backup, first of all enter Owner Name, Device Evidence Number and
Owner Phone Number.
Click
on Browse Option to select the path
folder where backup data will be stored and click on Next.
Now it will ask for part of file system to backup. Choose Whole File System or Specified
File Types such as Audio, Video or pictures. Then Click on Next.
Now it will show the progress bar for Back Up and after
completion click on Next.
Now select the check box for Phone memory extraction and click on Next.
Now it will show the message for creation of memory dump on
memory card file. Click on Next.
Now select the group….Cases
to organize device data or click on <New
Case > to create new case and click on Next.
If
we have selected New Case Option, then it will ask for Case Number and
investigator details .Enter
Investigator Details and click on Next.
Now select the Template for Data Export and Click on Finish.
Now select the Template for Data Export and Click on Finish.
Now it will show the generated Forensic Report.
Select Connected Device Option.
Now it will generate a report with all the details such as
Phone book, Call logs, messages, Files etc.
To get phone book details, select Phone book option.
Now you can select sub option such as WhatApp to see
WhatsApp Messages.
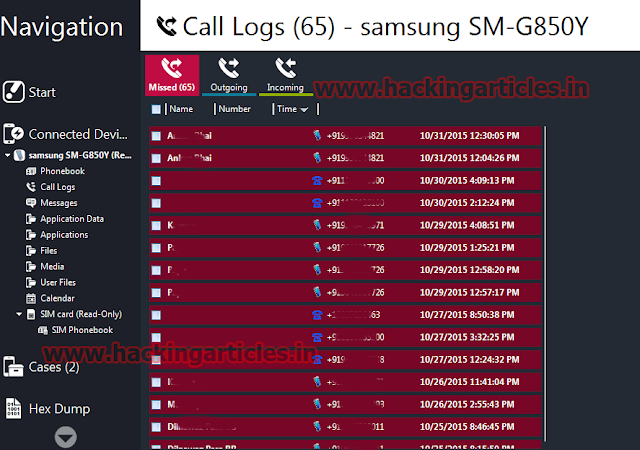
Click on Call Logs to see Missed Calls, Outgoing calls and
Incoming calls.
Now Click on Messages to see all received, sent and draft
messages.
Click on Application Data to get all the details about
content providers.
Click on Application to see all the installed Apps in
Mobile.
Select Files Option to see all the details about system
files in Mobile.
Now Click on Media and select internal media or user media
and then select pictures option to see Pictures.
To view User‘s Files, Click on Option User Files.