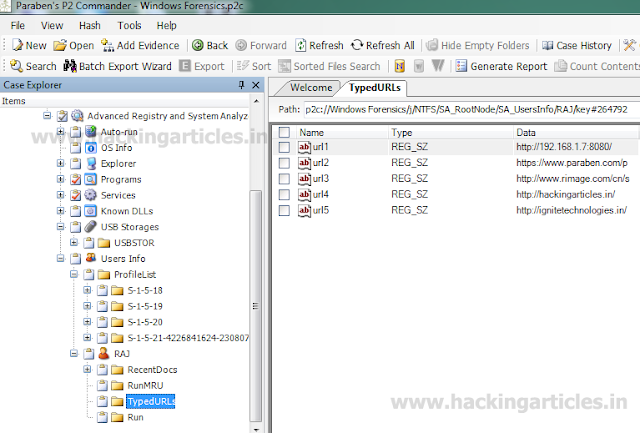
The
ARC Group ProDiscover® Basic edition is a self-managed tool for the examination
of your hard disk security. ProDiscover Basic is designed to operate under the
National Institute of Standards’ Disk Imaging Tool Specification 3.1.6 to
collect snapshots of activities that are critical to taking proactive steps in
protecting your data.
ProDiscover
Basic has a built-in reporting tool to present findings as evidence for legal
proceedings. You gather time zone data, drive information, Internet activity,
and more, piece by piece, or in a full report as needed. You have robust search
capabilities for capturing unique data, filenames and filetypes, data patterns,
date ranges, etc. ProDiscover Basic gives clients the autonomy they desire in
managing their own data security.
At
the ARC Group, we provide the tools you need to identify security issues before
they escalate, and we use ProDiscover solutions to maintain your corporate
safety and preserve your data. With ProDiscover Basic, professional
consultants, system administrators, and investigators take the upper hand to
manage cyber security at every level and protect information in the case of
impending legal actions.
First
Download the ProDiscover Basic from here and
install it in pc and enter the Project
Number, Project File Name and Description in prodiscover basic software.
Click on Open.
In main window click on Capture & Add Image
Now select the
source drive that we want to capture, this could be a USB Drive or physical
Drive.In my case I select drive Physical
Drive 1 which is my USB drive.
Now set the destination of the image file where we want to store it, in my case I used E: drive and named the image folder as pd and the name of the image which is to be saved in desired folder is PD.EVE .
Now enter the ‘Technician Name’, ‘Image Number’ and ‘description’ Now Click on ok.
After finishing the following steps, windows will appear.
After
imaging the drive close the prodiscover
program then it will ask you to save your project.
Now
starts prodiscover program again and click on open project and browser your project image select it and click open
Now the
project will open & go to the left menu and click on Content View. Then it will show you all the contents of evidence image.
To generate
the automatic report click on report
tab under the view menu. Then it
will show you Evidence Report.