Hello friends! Today you will learn how to setup VOIP in
virtual machine using tribox 2.8.0.4
iso image for making phone calls and sending text messages in local network.
From Wikipedia
Voice
over Internet Protocol (also voice over IP, VoIP or IP
telephony) is a methodology and group of technologies for the delivery of voice
communications and multimedia sessions over Internet
Protocol (IP)
networks, such as the Internet.
Let’s start!!
Open vmware, select option
“creates new virtual machine”, now for install from wizard select third option:
I will install operating system later
Then click on next.
Now select 2nd option “Linux” for guest operating system and select version “ubuntu”. Then click on next and next as
per your requirements.
Explore custom hardware for making following changes:
Click on
CD/DVD to browse ISO file “tribox
2.8.0.4”.
Select bridges
connection and enable the check box for replicate connection for network
adapter setting.
Then click on finish.
Trixbox is the world's most popular
Asterisk-based distribution. Trixbox enables even the novice user to quickly
set up a voice over IP phone system and other necessary applications such as
mysql and more. Trixbox can be configured to handle a single phone line for a
home user, several lines for a small office, or several T1s for a million
minute a month call center.
It will start rebooting the vm automatically, now for TRIBOX
CE installation follow given below steps:
A dialog box will appear for selecting option keyboard type, here chose option “US” as given in below image. Then click
on OK tab.
Another dialog fox will ask to choose time zone, select Asia/ Kolkata. Then click on OK tab.
Now enter the
password you want to give for root user. I had given
tribox as password. Again type confirm
password and then click on
OK tab.
Now it will start installation process automatically which
will take some time as shown in given below image. Do not disturb installation until
it becomes 100 % completely.
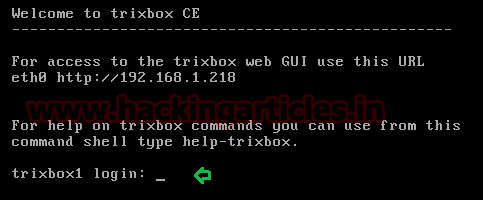
Once installation will complete it will ask for login. Type username: root and password: tribox
Check network interface using “ifconfig” command, now from
here I came to know my vm IP:
192.168.1.128.
Now open this IP: 192.168.1.218 in web browser. Here
through Tribox GUI we are going to create some users account by assigning them extension
number. For example you received 8 digit numbers for your land-line from
service providers.
By default tribox GUI open with user mode and for
creating extension number we need to switch into admin mode.
Click on switch
option for user mode given on top of right corner.
The authentication is required for login into admin mode
of tribox.
Now enter username:
maint and password: password as
admin credential.
You will get a pop up message for tribox registration, close
this message.
At tribox platform you will see server status, now click on PBX option and select PBX setting option from given menu.
Under setup list of admin
select extensions option as basic
setup.
Select device
Now follow given below steps for creating an extension
inside the server:
Device: generic SIP device
Click on submit
Add extension
User extension: 1234567 (any 7 digit number)
Display name: ignite (name of user/ customer you want
assign this number)
Device options
Secret: 123
Dtmfmode: rfc2833
Once you have enter the information for creating a new
extension click on submit.
Similarly create one more extension so then we can check
communication between both extensions.
From given image you can see now we had configured two
extension 1st for ignite
[1234567] and 2nd for raj[12345678].
We had created two extensions one as caller and other as
receiver. You can create multiple extension as per your requirement.
Now click on orange color tile for apply configuration
changes to put them into effect.
A pop will open here select continue with reload
Now
this is all about server installation and configuration of extension inside it.
Now download
ZOIPER application in your system
Zoiper is a VoIP softphone
that lets you send messages, make voice and video calls with your friends,
family, colleagues and business partners.
Once it is downloaded it
will look like as given below image, now go with setting option for configuration of an account which will be able
to make call or receive call from another user.
Select account type SIP
and click on next.
If you remember in tribox GUI we had add an extension
1234567 for ignite now enter those information in account wizard in order to
save it as new contact.
Now enter user number with server IP as given below
Enter password for this account of your own choice.
Click on next.
It will auto detect the account name as shown in given
image. Then click on next.
Your one account has been created in accounted list. Now
ignite will be able to make calls or receive calls from another users.
We have already created ignite account in system through
zoiper for making and receiving calls. Now we need to install zoiper on other
device for other users also, who will be able to make or receive call from
ignite.
Download zoiper from Google
play stores in your android phone.
Run the application after installation.
Click on config icon
for configuration of a new account in your phone as shown in given image and
select Accounts option from given
list of configuration.
Now again a new dialog box will pop up select manual configuration for account setup.
Account name: raj
Host: 192.168.1.218
Username: 12345678
Password: 123
Now click on save.
You can see from given image that account for raj is ready.
Hence we have setup two accounts in zoiper one will act as
caller let say raj is caller making
call to ignite through his phone and ignite
will be receiver and get incoming call on system from raj.
As you know we had configured two extension one for ignite
another for raj. Now we are going to test this VOIP setup by making call from raj.
Raj had made call to ignite by dialing his number 1234567 and when you will perform this
you will hear the outgoing bell from your phone.
Ignite will get incoming call on system as shown in given
image. Click on answer for accepting call from raj.
From given screenshot you can see that the call is connected
and raj and ignite is having conversation over VOIP call.
Great!!! Hence in
this way you can configure your VOIP server for local network and can
communicate with multiple users by making calls or chat.